U
UFHH01
Guest
Hi D4NY,
o.k. - let's start with some suggestions here:
Your servers hostname is configured with "nsXXXXXX.ip-XX-XX-XXX.eu", while you secured your mail - server with the certificate from "mail.XXXXXXXXXX.eu".
o.k. - let's start with some suggestions here:
Your servers hostname is configured with "nsXXXXXX.ip-XX-XX-XXX.eu", while you secured your mail - server with the certificate from "mail.XXXXXXXXXX.eu".
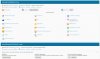
This can be solved by changing the servers hostname at => HOME > Tools & Settings > Server Settings to for example "YOUR-DESIRED-NAME.XXXXXXXXXX.eu".
Afterwards, pls. check your new settings over the command line with the command ( logged in as uer "root" over SSH ):
Let's assume now, that you choosed a servername like "servername.YOUR-DOMAIN.COM", then pls. add the corresponding SUBDOMAIN - name "servername" at the domain - specific subscription of "YOUR-DOMAIN.COM".
( if not already done! ) Pls. add afterwards a SUBDOMAIN "mail.YOUR-DOMAIN.COM".
Secure BOTH of the subdomains with the help of the Plesk Let's Encrypt Extension and you should now have two valid certificates for "servername.YOUR-DOMAIN.COM" and "mail.YOUR-DOMAIN.COM".
You are now able to secure your Plesk Control Panel and the mail - server with these two certificates at: => HOME > Tools & Settings > SSL/TLS Certificates
The next step is to CHANGE YOUR REVERSE for your IP. This is done over the Control Panel of your server provider OVH. Instructions I found are:
To continue, pls. check now the file "/etc/hosts" on your server and correct it to for example:
To be sure, that all your postfix and dovecot configuration files are correct, pls use now the Plesk Repair Utility with the command:
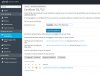
At the end, you should now consider to modify as well the SPF - entry for your domain(s), which can be easily be done at:
=> HOME > Tools & Settings > DNS Template

It may take some hours, untill the new reverse entry for your IP and the DNS - changes are synced with the worldwide nameservers... so pls. check for example with the help of the following links, if all your changes are in place:
=> DNS Lookup for 94.XXX.XXX.204
=> DNS Lookup for YOUR-DOMAIN.COM
If all is fine and in place, pls. send now with your desired eMail - Client an eMail to any external eMail - adress and send an eMail from this external eMail - adress to any eMail - account, setup over your own server and check the "mail.log" afterwards, to see the results.
If you experience further issues/errors/problems, pls. include the NEW "mail.log" and the NEW configuration files "main.cf", "master.cf" from postfix and as well the NEW configuration file from dovecot ( /etc/dovecot/dovecot.conf ) as attachments to your post.
Afterwards, pls. check your new settings over the command line with the command ( logged in as uer "root" over SSH ):
Code:
hostnameLet's assume now, that you choosed a servername like "servername.YOUR-DOMAIN.COM", then pls. add the corresponding SUBDOMAIN - name "servername" at the domain - specific subscription of "YOUR-DOMAIN.COM".
( if not already done! ) Pls. add afterwards a SUBDOMAIN "mail.YOUR-DOMAIN.COM".
Secure BOTH of the subdomains with the help of the Plesk Let's Encrypt Extension and you should now have two valid certificates for "servername.YOUR-DOMAIN.COM" and "mail.YOUR-DOMAIN.COM".
You are now able to secure your Plesk Control Panel and the mail - server with these two certificates at: => HOME > Tools & Settings > SSL/TLS Certificates
The next step is to CHANGE YOUR REVERSE for your IP. This is done over the Control Panel of your server provider OVH. Instructions I found are:
=> OVH : PersonalisedReverse
Due to the fact, that you choosed "servername.YOUR-DOMAIN.COM" for your servers hostname, the reverse of the IP "94.XXX.XXX.204" should now point to the new hostname!
Due to the fact, that you choosed "servername.YOUR-DOMAIN.COM" for your servers hostname, the reverse of the IP "94.XXX.XXX.204" should now point to the new hostname!
To continue, pls. check now the file "/etc/hosts" on your server and correct it to for example:
Code:
127.0.0.1 localhost.localdomain localhost
127.0.0.1 servername.YOUR-DOMAIN.COM servername
94.XXX.XXX.204 servername.YOUR-DOMAIN.COM servernameTo be sure, that all your postfix and dovecot configuration files are correct, pls use now the Plesk Repair Utility with the command:
Code:
plesk repair mail -y -vAt the end, you should now consider to modify as well the SPF - entry for your domain(s), which can be easily be done at:
=> HOME > Tools & Settings > DNS Template
At the moment you use "v=spf1 include:turbo-smtp.com ?all" and you should consider to use as template the TXT - entry:
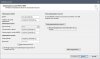
Apply the changes and head over to your domain - specific DNS - settings at:
As I don't know right now, if you use an external nameserver, where you should place the very same DNS - entries as you see them over your domain specific DNS - Settings at your Plesk Control Panel, I suggest now, not to forget to modify/add/edit all the above DNS - changes at the Control Panel from your domain - provider.
Code:
v=spf1 +mx +a a:<hostname> include:turbo-smtp.com ip4:94.XXX.XXX.204 ?all=> HOME > Subsciptions > YOUR-DOMAIN.COM > DNS Settings
... and check that your changes are set to the SPF - TXT - entry to:
... and check that your changes are set to the SPF - TXT - entry to:
Code:
v=spf1 +mx +a a:servername.YOUR-DOMAIN.COM include:turbo-smtp.com ip4:94.XXX.XXX.204 ?allIt may take some hours, untill the new reverse entry for your IP and the DNS - changes are synced with the worldwide nameservers... so pls. check for example with the help of the following links, if all your changes are in place:
=> DNS Lookup for 94.XXX.XXX.204
=> DNS Lookup for YOUR-DOMAIN.COM
If all is fine and in place, pls. send now with your desired eMail - Client an eMail to any external eMail - adress and send an eMail from this external eMail - adress to any eMail - account, setup over your own server and check the "mail.log" afterwards, to see the results.
If you experience further issues/errors/problems, pls. include the NEW "mail.log" and the NEW configuration files "main.cf", "master.cf" from postfix and as well the NEW configuration file from dovecot ( /etc/dovecot/dovecot.conf ) as attachments to your post.