- Server operating system version
- Debian 11
- Plesk version and microupdate number
- 18.0.61
Hello,
I found a very nice article in plesk blog to block badbots with fail2ban. I have problems with ClaudeBot who is hitting the server all the time.
The problem is that I have some problems with the article.
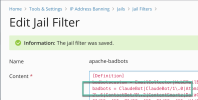
First I edited /etc/fail2ban/filter.d/apache-badbots.conf as requested adding the line:
badbots = ClaudeBot|ClaudeBot/1\.0
As I want to block this bot only (as a test)
and then reload:
But I have an error:
2024-05-30 17:33:30,944 fail2ban [1464544]: ERROR Failed during configuration: No section: 'plesk-apache-badbots'
If you don´t tuch anything (in another server) and reload I received the same error.
So I checked again the file /etc/fail2ban/jail.local as the article say and the section in the file is called:
[plesk-apache-badbot]
And not
[plesk-apache-badbots]
(note the s)
So I added the lines under [plesk-apache-badbot] and restart:
Without an s. All ok now (it seems the article have this error), but when I test the filter:
The result is:
Lines: 7163 lines, 0 ignored, 0 matched, 7163 missed
So no line is checked...
So I can´t block the bot in the server. Any ideas?
I found a very nice article in plesk blog to block badbots with fail2ban. I have problems with ClaudeBot who is hitting the server all the time.
The problem is that I have some problems with the article.
First I edited /etc/fail2ban/filter.d/apache-badbots.conf as requested adding the line:
badbots = ClaudeBot|ClaudeBot/1\.0
As I want to block this bot only (as a test)
and then reload:
fail2ban-client reload plesk-apache-badbots
But I have an error:
2024-05-30 17:33:30,944 fail2ban [1464544]: ERROR Failed during configuration: No section: 'plesk-apache-badbots'
If you don´t tuch anything (in another server) and reload I received the same error.
So I checked again the file /etc/fail2ban/jail.local as the article say and the section in the file is called:
[plesk-apache-badbot]
And not
[plesk-apache-badbots]
(note the s)
So I added the lines under [plesk-apache-badbot] and restart:
fail2ban-client reload plesk-apache-badbot
Without an s. All ok now (it seems the article have this error), but when I test the filter:
fail2ban-regex /var/www/vhosts/domain.com/logs/access_ssl_log /etc/fail2ban/filter.d/apache-badbots.conf
The result is:
Lines: 7163 lines, 0 ignored, 0 matched, 7163 missed
So no line is checked...
So I can´t block the bot in the server. Any ideas?