Hi. I have a problem with LetsEncrypt certificates for each domain (only for mail). This works fine for sites. For mail, it gets the server's root certificate instead of the domain. Why?
Example:
openssl s_client -showcerts -servername bezglutenowyhert.pl -connect bezglutenowyhert.pl:465
This is my settings. It looks correct.
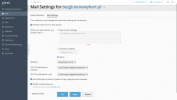
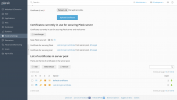
Example:
openssl s_client -showcerts -servername bezglutenowyhert.pl -connect bezglutenowyhert.pl:465
This is my settings. It looks correct.





