Solved! CloudFlare config: Cómo comprender HSTS (HTTP Strict Transport Security)
-
We value your experience with Plesk during 2025
Plesk strives to perform even better in 2026. To help us improve further, please answer a few questions about your experience with Plesk Obsidian 2025.
Please take this short survey:
https://survey.webpros.com/
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Resolved SSL It - HSTS appearing twice in headers
- Thread starter thinkingcap
- Start date
g.u.r.k.a.n
New Pleskian
We would appreciate it you share some additional details regarding your server/domain/settings, e.g.
- What OS and Plesk versions are used?
- What version of SSL It! is installed?
- Do you use Cloudflare or something similar in front of a website?
- What other headers present in the server's response? URL?
- How do you check headers, what tool / online resource?
Maybe added by an additional directive in either the web server configuration page or by an entry in .htaccess?
g.u.r.k.a.n
New Pleskian
We would appreciate it you share some additional details regarding your server/domain/settings, e.g.
I have checked two of my websites (one of them is connected to Cloudflare) with laptop's browser (and with at least two online tools) and do not found doubled HSTS headers.
- What OS and Plesk versions are used?
- What version of SSL It! is installed?
- Do you use Cloudflare or something similar in front of a website?
- What other headers present in the server's response? URL?
- How do you check headers, what tool / online resource?
- I use a shared server hosting and the server uses Plesk for Windows 18.0.34 according the support team.
- I use Let's Encrypt R3 SSL cert.
- I don't use cloudflare or similar tunnel or something else.
- I use almost 20 header for CORS.
- I'm a developer and I'm coding everything myself in the website backend/frontend. I don't use a tool. I check these headers from direct browser console. By the way, I also manually add all the other headers myself and the others are adding properly only once.
Last edited by a moderator:
g.u.r.k.a.n
New Pleskian
Thanks Peter, I don't use any php, I use just .NETMaybe added by an additional directive in either the web server configuration page or by an entry in .htaccess?
@g.u.r.k.a.n, thank you very much for the detailed answer, many details usually help a lot!
I can confirm that I see two HTST headers in browser's console for your domain.
The first thing that alerted me was that you are using an old version of Plesk, apparently the last update was made 3 years ago. I guess this is due to the legacy operational system, which has also reached its EOL state. Unfortunately, because of this, I cannot check for a bug on the versions you are using, these versions are not supported. And even if we confirm and fix the bug, you will not be able to install the fixed version on your system until you update your system and Plesk to supported versions.
Anyway, I will try to reproduce the bug on Windows Server 2022 with Plesk 18.0.59 (with SSL It! 1.14.6, Let's Encrypt 3.2.4) and come back with a result.
I can confirm that I see two HTST headers in browser's console for your domain.
The first thing that alerted me was that you are using an old version of Plesk, apparently the last update was made 3 years ago. I guess this is due to the legacy operational system, which has also reached its EOL state. Unfortunately, because of this, I cannot check for a bug on the versions you are using, these versions are not supported. And even if we confirm and fix the bug, you will not be able to install the fixed version on your system until you update your system and Plesk to supported versions.
Anyway, I will try to reproduce the bug on Windows Server 2022 with Plesk 18.0.59 (with SSL It! 1.14.6, Let's Encrypt 3.2.4) and come back with a result.
Last edited:
g.u.r.k.a.n
New Pleskian
@AYamshanov, then the currently running version definitely already has this bug. I'm in touch with the hosting firm. I will share link of this thread with them and ask them to upgrade for plesk and SSL certification.
From https://docs.plesk.com/release-notes/obsidian/change-log link I see that the latest version is 18.0.59 Update 2. I hope the other softwares running on the server fulfil the requirements. I also thank you for your interest.
From https://docs.plesk.com/release-notes/obsidian/change-log link I see that the latest version is 18.0.59 Update 2. I hope the other softwares running on the server fulfil the requirements. I also thank you for your interest.
I have checked on the latest versions (Windows 2022, Plesk 18.0.59), as you can see, there is only one HSTS header,
So, from my side, I would suggest doing the next steps,

So, from my side, I would suggest doing the next steps,
- verify that nothing (except Plesk) adds HSTS headers on the website and/or server side,
- try to reproduce the issue on the updated (and supported) environment, sort of staging environment,
- If it reproducible, share with us steps to reproduce, it will help investigate the issue faster.
Also, when you use supported versions, it should be possible to contact the Support team to investigate the issue on the server. - If the issue disappear on the latest versions, makes sense to plan upgrading to the latest versions.
- If it reproducible, share with us steps to reproduce, it will help investigate the issue faster.
g.u.r.k.a.n
New Pleskian
@AYamshanov, the 2 years in the picture you attached is actually the best practice for the header. Actually, if I turn off HSTS, the duplicate one is not added, but this is not a solution for me. Because I want to change it to 2 years or at least 6 months, not the default value.
In short, if the certificate HSTS is turned off, it overrides the value I send manually, and when it is turned on, it adds it with the value I sent. So in this case, the issue is not only that it is duplicate, but also that the value sent is being overrided.
For a complete solution, I think you, the Plesk Team, should add a numeric option for max-age value in Plesk for the header to next versions.
In short, if the certificate HSTS is turned off, it overrides the value I send manually, and when it is turned on, it adds it with the value I sent. So in this case, the issue is not only that it is duplicate, but also that the value sent is being overrided.
For a complete solution, I think you, the Plesk Team, should add a numeric option for max-age value in Plesk for the header to next versions.
hm... Does this mean that you are actually manually sending another header in addition to the one that Plesk adds?
And if you want to change "max-age" to "2 years", could you please check HSTS settings in the "SSL It!" extension and select the last item in the list? I hope it should help to solve the initial issue.
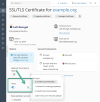
And if you want to change "max-age" to "2 years", could you please check HSTS settings in the "SSL It!" extension and select the last item in the list? I hope it should help to solve the initial issue.

g.u.r.k.a.n
New Pleskian
@AYamshanov the problem is already exact this option  I cannot override it. When I turn on the HSTS only the time value should change.
I cannot override it. When I turn on the HSTS only the time value should change.
HSTS off

HSTS on (In this case I don't want the first one)
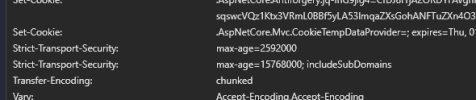
HSTS off

HSTS on (In this case I don't want the first one)

I don't understand where the first value comes from (2592000 secs = 30 days). If it is set manually somewhere in the website code, makes sense to remove it and enable HSTS in the Plesk only.
At the moment I think that there is no bug in Plesk. Theoretically, it could be some kind of a feature request to allow Plesk to override the headers but don't remember someone else asking about such feature (also not sure about technical possibility to do that, some research is required).
At the moment I think that there is no bug in Plesk. Theoretically, it could be some kind of a feature request to allow Plesk to override the headers but don't remember someone else asking about such feature (also not sure about technical possibility to do that, some research is required).
g.u.r.k.a.n
New Pleskian
@AYamshanov
I said that "You should add an option" because the plesk is in the last point in any request. I mean, even browsers may also take responsibility for this case in the next years.
I don't want to slow down it, but if this issue bothers me more, I'm going to temporarily manually remove this automatically added header with extra lines of code Thanks for your interest.
Thanks for your interest.
I can't find it either. The isn't any Strict-Transport-Security header when I debug on development envorinment. And also, I have added almost all headers as I said before and I don't add Strict-Transport-Security on the dev. It's just added in the product environment in a way I don't understand.I don't understand where the first value comes from
I said that "You should add an option" because the plesk is in the last point in any request. I mean, even browsers may also take responsibility for this case in the next years.
I don't want to slow down it, but if this issue bothers me more, I'm going to temporarily manually remove this automatically added header with extra lines of code
@AYamshanov
This issue is current today:
We would appreciate it you share some additional details regarding your server/domain/settings, e.g.
What OS and Plesk versions are used? --> Ubuntu 22 and Plesk Obsidian v18.0.61
What version of SSL It! is installed? --> 1.15.3-3574
Do you use Cloudflare or something similar in front of a website? --> No.
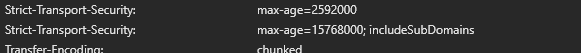
What other headers present in the server's response? URL? --> Please see attached text file. (edit: Plesk forum doesn't allow text uploads. Picture attached. )
How do you check headers, what tool / online resource --> HTTP Header and Status Checker
Edit: We have not put in place any special tweaks to the plesk code, simply used the SSL it! Extension standard interface.
This issue is current today:
We would appreciate it you share some additional details regarding your server/domain/settings, e.g.
What OS and Plesk versions are used? --> Ubuntu 22 and Plesk Obsidian v18.0.61
What version of SSL It! is installed? --> 1.15.3-3574
Do you use Cloudflare or something similar in front of a website? --> No.
What other headers present in the server's response? URL? --> Please see attached text file. (edit: Plesk forum doesn't allow text uploads. Picture attached. )
How do you check headers, what tool / online resource --> HTTP Header and Status Checker
Edit: We have not put in place any special tweaks to the plesk code, simply used the SSL it! Extension standard interface.
Attachments
@AYamshanov
This issue is current today:
We would appreciate it you share some additional details regarding your server/domain/settings, e.g.
What OS and Plesk versions are used? --> Ubuntu 22 and Plesk Obsidian v18.0.61
What version of SSL It! is installed? --> 1.15.3-3574
Do you use Cloudflare or something similar in front of a website? --> No.
What other headers present in the server's response? URL? --> Please see attached text file. (edit: Plesk forum doesn't allow text uploads. Picture attached. )
How do you check headers, what tool / online resource --> HTTP Header and Status Checker
Edit: We have not put in place any special tweaks to the plesk code, simply used the SSL it! Extension standard interface.
UPDATE:
Upon closer inspection found that the HSTS was set by a plugin within the WordPress. This was causing the double setting.
I had the same problem where the HSTS header was appearing twice:
We use a redirect via vhost.conf as we are using Varnish. Using the Plesk option "Redirect from http to https" has side effects in those case.
I then noticed that the header is set for https and http:
Plesk Support examined the problem and came to this conclusion:
Hope this helps someone ;-)
Interestingly, querying without "www" showed this:myhost:~# curl -s -IXGET Example Domain | grep strict
strict-transport-security: max-age=63072000; includeSubDomains
strict-transport-security: max-age=63072000; includeSubDomains
myhost:~# curl -s -IXGET Example Domain | grep strict
strict-transport-security: max-age=63072000; includeSubDomains
We use a redirect via vhost.conf as we are using Varnish. Using the Plesk option "Redirect from http to https" has side effects in those case.
I then noticed that the header is set for https and http:
myhost:~# grep strict /var/www/vhosts/system/example.com/conf/httpd.conf
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains"
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains"
Plesk Support examined the problem and came to this conclusion:
It appears that this behavior is observed when the Redirect from http to https option is disabled and HSTS is enabled.
The development team confirmed that this is a bug. An internal task has been created and the bug is with ID: EXTSSLIT-2167.
Until the bug is fixed, one of the following two workarounds can be applied:
1) Enable the Redirect from http to https option in Domains > example.com > SSL/TLS Certificates.
2) Manually enable HSTS via additional HTTPS settings, for example:
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains; preload"
Hope this helps someone ;-)
Similar threads
- Replies
- 2
- Views
- 452
- Replies
- 2
- Views
- 5K
- Replies
- 9
- Views
- 7K
- Replies
- 5
- Views
- 3K