- Server operating system version
- Debian 11
- Plesk version and microupdate number
- 18.0.54
Hi.
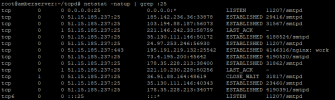
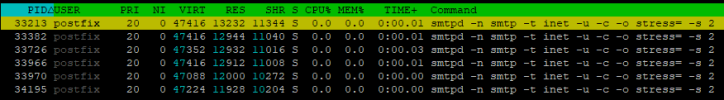
I've recently observed quite a large amount of outgoing connections from port 25 to numerous (malicious?) IP's through postfix, in turn creating several rather strange smtpd processes. I think they are bad bots. I'm mass banning them via fail2ban in the plesk-postfix part every time they do something, but they seem to be endless.
Are these connections harmful? Is there a way to prevent them from occurring? Can they cause me to enter blacklists like Spamhaus.org?
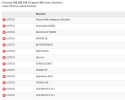
I attach images of the command used "netstat -natup | grep :25" where these connections can be seen, also of the "htop" command where said processes are executed, and also of the result of the mxtoolbox.com blacklists when entering any of these IP's.
Thank you so much.
I've recently observed quite a large amount of outgoing connections from port 25 to numerous (malicious?) IP's through postfix, in turn creating several rather strange smtpd processes. I think they are bad bots. I'm mass banning them via fail2ban in the plesk-postfix part every time they do something, but they seem to be endless.
Are these connections harmful? Is there a way to prevent them from occurring? Can they cause me to enter blacklists like Spamhaus.org?
I attach images of the command used "netstat -natup | grep :25" where these connections can be seen, also of the "htop" command where said processes are executed, and also of the result of the mxtoolbox.com blacklists when entering any of these IP's.
Thank you so much.