- Server operating system version
- Debian 10.13
- Plesk version and microupdate number
- 18.0.69 Update #2
Hi there
As the title says, i have a problem with custom webapp fw rules on a custom domain (so not in the general webapp fw settings section)
Get that message...
*****************************************************
Die folgenden Werte sind nicht gültig: SecRule REQUEST_URI|ARGS_NAMES "@contains Chitoge" "id:1001001, phase:1, deny, status:403, msg:Blocked Chitoge Access", SecRule ARGS_NAMES "@rx ^(Chitoge|Gorila|Kirisaki|idx_file|upload)$" "id:1001002, phase:1, deny, status:403, msg:Suspicious parameter", SecRule REQUEST_BODY "@rx eval base64_decode" "id:1001003, phase:2, deny, status:403, msg:Blocked Obfuscated Payload", SecRule REQUEST_URI "@rx ^.*wp-content|uploads|images|cache.*\.(php|phtml)$" "id:1001004, phase:1, deny, status:403, msg:Suspicious file path", SecRule REQUEST_METHOD "POST" "chain, id:1001005, phase:1, deny, status:403, msg:Suspicious file upload", SecRule REQUEST_HEADERS:Content-Type "@contains multipart/form-data" "msg:Multipart form data detected". Die Regelnachricht darf nur Buchstaben, Ziffern, Leerzeichen und die folgenden Zeichen enthalten: -:;.,!?#&$%*()/.
Nur genaue Übereinstimmungen werden unterstützt.
*****************************************************
...when i try to add that rules:
Screenshot here:
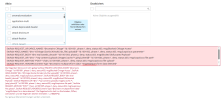
Why?
Thank you very much for your feedback(s).
As the title says, i have a problem with custom webapp fw rules on a custom domain (so not in the general webapp fw settings section)
Get that message...
*****************************************************
Die folgenden Werte sind nicht gültig: SecRule REQUEST_URI|ARGS_NAMES "@contains Chitoge" "id:1001001, phase:1, deny, status:403, msg:Blocked Chitoge Access", SecRule ARGS_NAMES "@rx ^(Chitoge|Gorila|Kirisaki|idx_file|upload)$" "id:1001002, phase:1, deny, status:403, msg:Suspicious parameter", SecRule REQUEST_BODY "@rx eval base64_decode" "id:1001003, phase:2, deny, status:403, msg:Blocked Obfuscated Payload", SecRule REQUEST_URI "@rx ^.*wp-content|uploads|images|cache.*\.(php|phtml)$" "id:1001004, phase:1, deny, status:403, msg:Suspicious file path", SecRule REQUEST_METHOD "POST" "chain, id:1001005, phase:1, deny, status:403, msg:Suspicious file upload", SecRule REQUEST_HEADERS:Content-Type "@contains multipart/form-data" "msg:Multipart form data detected". Die Regelnachricht darf nur Buchstaben, Ziffern, Leerzeichen und die folgenden Zeichen enthalten: -:;.,!?#&$%*()/.
Nur genaue Übereinstimmungen werden unterstützt.
*****************************************************
...when i try to add that rules:
Code:
SecRule REQUEST_URI|ARGS_NAMES "@contains Chitoge" "id:1001001, phase:1, deny, status:403, msg:Blocked Chitoge Access"
SecRule ARGS_NAMES "@rx ^(Chitoge|Gorila|Kirisaki|idx_file|upload)$" "id:1001002, phase:1, deny, status:403, msg:Suspicious parameter"
SecRule REQUEST_BODY "@rx eval base64_decode" "id:1001003, phase:2, deny, status:403, msg:Blocked Obfuscated Payload"
SecRule REQUEST_URI "@rx ^.*wp-content|uploads|images|cache.*\.(php|phtml)$" "id:1001004, phase:1, deny, status:403, msg:Suspicious file path"
SecRule REQUEST_METHOD "POST" "chain, id:1001005, phase:1, deny, status:403, msg:Suspicious file upload"
SecRule REQUEST_HEADERS:Content-Type "@contains multipart/form-data" "msg:Multipart form data detected"Screenshot here:

Why?
Thank you very much for your feedback(s).
