brother4
Basic Pleskian
- Server operating system version
- Ubuntu 22.04
- Plesk version and microupdate number
- Plesk Obsidian 18.0.64 Web Host Edition
Hello!
I've been using the WordPress jail in Fail2Ban to protect my WordPress installations from brute-force attacks. While I appreciate the protection it offers, I recently noticed a significant gap in its coverage that raises some concerns regarding security.
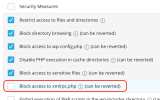
Specifically, I’ve observed thousands of POST requests targeting xmlrpc.php on several WordPress instances. These frequent requests are often used for brute-force attacks, exploiting the system.multicall method to test multiple login credentials in a single request.
While it’s good practice to disable or block xmlrpc.php via .htaccess, this isn’t commonly done by default, especially for less experienced users. Therefore, I believe the WordPress jail in Plesk should extend its monitoring to include suspicious activities related to xmlrpc.php as well. As it stands, this critical file seems to be outside the scope of the current jail filter, which primarily focuses on /wp-login.php attacks.
Given that Fail2Ban suggests it protects against brute-force attacks for WordPress, shouldn't this protection encompass xmlrpc.php, given its known vulnerabilities? I think this poses a major security risk, especially for users who trust Plesk's default protections to keep their sites safe without further customization.
Is there any plan to enhance the filters to cover attacks on xmlrpc.php? It seems essential, considering how common these attacks are.
Looking forward to hearing your thoughts on this!
I've been using the WordPress jail in Fail2Ban to protect my WordPress installations from brute-force attacks. While I appreciate the protection it offers, I recently noticed a significant gap in its coverage that raises some concerns regarding security.
Specifically, I’ve observed thousands of POST requests targeting xmlrpc.php on several WordPress instances. These frequent requests are often used for brute-force attacks, exploiting the system.multicall method to test multiple login credentials in a single request.
While it’s good practice to disable or block xmlrpc.php via .htaccess, this isn’t commonly done by default, especially for less experienced users. Therefore, I believe the WordPress jail in Plesk should extend its monitoring to include suspicious activities related to xmlrpc.php as well. As it stands, this critical file seems to be outside the scope of the current jail filter, which primarily focuses on /wp-login.php attacks.
Given that Fail2Ban suggests it protects against brute-force attacks for WordPress, shouldn't this protection encompass xmlrpc.php, given its known vulnerabilities? I think this poses a major security risk, especially for users who trust Plesk's default protections to keep their sites safe without further customization.
Is there any plan to enhance the filters to cover attacks on xmlrpc.php? It seems essential, considering how common these attacks are.
Looking forward to hearing your thoughts on this!