- Server operating system version
- AlmaLinux 8.10
- Plesk version and microupdate number
- 18.0.67
Hi Guys
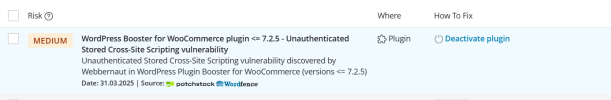
I while ago I reported incorrect risk values in WordPress Toolkits Vulnerability reports (as others did) and it is happening again, both of the below have risen from low to medium for no reason.
Thanks in advance for your help.
Cheers
Gary
I while ago I reported incorrect risk values in WordPress Toolkits Vulnerability reports (as others did) and it is happening again, both of the below have risen from low to medium for no reason.
- WordPress Core - Informational - All known Versions - Weak Hashing Algorithm - Date: 20.06.2012
All known versions of WordPress core use a weak MD5-based password hashing algorithm, which makes it easier for attackers to determine cleartext values by leveraging access to the hash values. NOTE: the approach to changing this may not be fully compatible with certain use cases, such as migration of a WordPress site from a web host that uses a recent PHP version to a different web host that uses PHP 5.2. These use cases are plausible (but very unlikely) based on statistics showing widespread deployment of WordPress with obsolete PHP versions. - WordPress Core - All Known Versions - Cleartext Storage of wp_signups.activation_key - Date: 10.10.2017
All known versions of WordPress Core store cleartext wp_signups.activation_key values (but stores the analogous wp_users.user_activation_key values as hashes), which might make it easier for remote attackers to hijack unactivated user accounts by leveraging database read access (such as access gained through an unspecified SQL injection vulnerability).
Thanks in advance for your help.
Cheers
Gary