- Server operating system version
- Debian 12.11
- Plesk version and microupdate number
- 18.0.69 Update 3
This morning (May 23, 2025), we observed that all our Plesk servers reported an error during the automatic update of system packages and third-party components. The following message was logged and also sent via email:
Additionally, the following warning is displayed in the Plesk interface:
“Warning: The information about some packages may not be up to date: Inconsistencies were found in the system package manager’s database. Please resolve this issue manually.”
Following the update errors that occurred on the morning of May 23, I performed a manual system check. The system showed no irregularities. During a manual update and upgrade process, no package changes were required, indicating that the system is up to date.
However, during the update, there was a warning related to one of the Plesk repositories. Specifically, the system was unable to access the package information from the RUBY_1.5.0 repository. The error pointed to a certificate verification issue, stating that the certificate is not trusted and the OCSP status response was invalid. As a result, the system could not complete a proper handshake with the server.
This suggests a temporary issue with the SSL certificate or its OCSP response on the Plesk side. All other repositories were contacted successfully, and the system appears fully updated despite the warning.
I would be interested to know if others are seeing the same behavior and whether Plesk has acknowledged the issue or provided any official guidance.
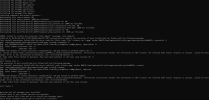
Code:
There was a problem updating the system packages and third-party components on the example.com server. Please wait for the next automatic update or start the update manually: https://example.com/admin/pum
Reason:
2025-05-23 06:25:52 INFO: pum is called with arguments: [’–update’, ‘–json’]
2025-05-23 06:26:00 ERROR: Apt cache fetch failed. Try to run the apt-get update command.
2025-05-23 06:26:00 ERROR:
2025-05-23 06:26:00 ERROR: Exited with return code 1.Additionally, the following warning is displayed in the Plesk interface:
“Warning: The information about some packages may not be up to date: Inconsistencies were found in the system package manager’s database. Please resolve this issue manually.”
Following the update errors that occurred on the morning of May 23, I performed a manual system check. The system showed no irregularities. During a manual update and upgrade process, no package changes were required, indicating that the system is up to date.
However, during the update, there was a warning related to one of the Plesk repositories. Specifically, the system was unable to access the package information from the RUBY_1.5.0 repository. The error pointed to a certificate verification issue, stating that the certificate is not trusted and the OCSP status response was invalid. As a result, the system could not complete a proper handshake with the server.
This suggests a temporary issue with the SSL certificate or its OCSP response on the Plesk side. All other repositories were contacted successfully, and the system appears fully updated despite the warning.
I would be interested to know if others are seeing the same behavior and whether Plesk has acknowledged the issue or provided any official guidance.
Code:
Ign:12 https://autoinstall.plesk.com/RUBY_1.5.0 bookworm InRelease
Ign:12 https://autoinstall.plesk.com/RUBY_1.5.0 bookworm InRelease
Err:12 https://autoinstall.plesk.com/RUBY_1.5.0 bookworm InRelease
Certificate verification failed: The certificate is NOT trusted. The received OCSP status response is invalid. Could not handshake: Error in the certificate verification. [IP: xxxx:xxxx:xxxx::xxx 443]
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
All packages are up to date.
W: Failed to fetch https://autoinstall.plesk.com/RUBY_1.5.0/dists/bookworm/InRelease Certificate verification failed: The certificate is NOT trusted. The received OCSP status response is invalid. Could not handshake: Error in the certificate verification. [IP: xxxx:xxxx:xxxx::xxx 443]
W: Some index files failed to download. They have been ignored, or old ones used instead.
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
Calculating upgrade... Done
The following package was automatically installed and is no longer required:
linux-image-6.1.0-28-amd64
Use 'apt autoremove' to remove it.
0 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.
Last edited by a moderator: