WhiteTiger
Basic Pleskian
- Server operating system version
- Ubuntu 22.04.1 LTS
- Plesk version and microupdate number
- 18.0.50
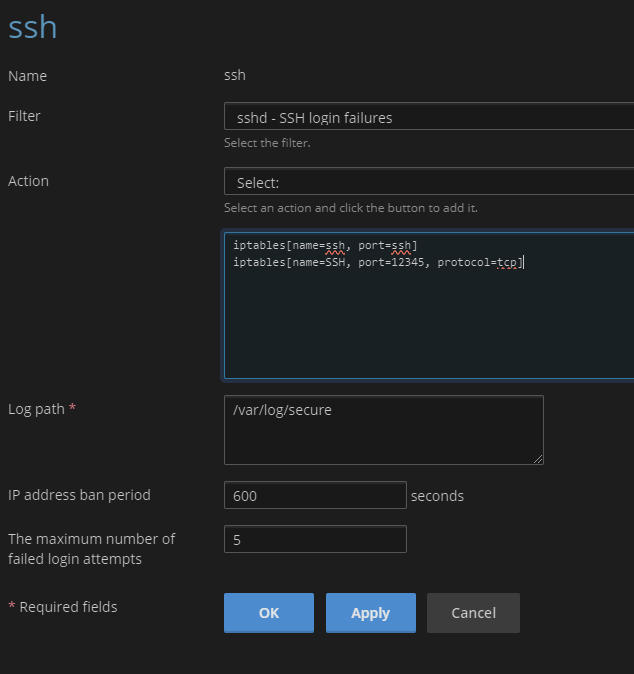
Access via SSH has been configured with a different port than 22.
How can I create a Fail2ban Jail to monitor it?
Can I copy the one for SSH and edit it?
How can I create a Fail2ban Jail to monitor it?
Can I copy the one for SSH and edit it?