- Server operating system version
- ubuntu 20.04
- Plesk version and microupdate number
- obsidian 18.0.50.2
filter:
[Definition]
failregex = ^<HOST>.* "POST .*/wp-login.php([/\?#\\].*)? HTTP/.*" 200
ignoreregex =
jail:
[plesk-wordpress]
enabled = true
filter = plesk-wordpress
action = iptables-multiport[name="wp-login", port="http,https", protocol="tcp"]
logpath = /var/www/vhosts/system/*/logs/*access*log
/var/log/apache2/*access.log
maxretry = 1
logs:
192.168.0.102 - - [27/Feb/2023:17:04:56 +0000] "POST /wp-login.php HTTP/1.0" 200 2886 "https://local.com/wp-login.php" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.0.0 Safari/537.36"
192.168.0.102 - - [27/Feb/2023:17:04:59 +0000] "POST /wp-login.php HTTP/1.0" 200 2885 "https://local.com/wp-login.php" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.0.0 Safari/537.36"
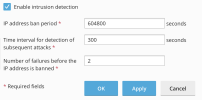
These are default values, i made sure fail2ban is enabled and that i am not in the white list, but anyways i don't get banned while bruteforcing wp-admin
[Definition]
failregex = ^<HOST>.* "POST .*/wp-login.php([/\?#\\].*)? HTTP/.*" 200
ignoreregex =
jail:
[plesk-wordpress]
enabled = true
filter = plesk-wordpress
action = iptables-multiport[name="wp-login", port="http,https", protocol="tcp"]
logpath = /var/www/vhosts/system/*/logs/*access*log
/var/log/apache2/*access.log
maxretry = 1
logs:
192.168.0.102 - - [27/Feb/2023:17:04:56 +0000] "POST /wp-login.php HTTP/1.0" 200 2886 "https://local.com/wp-login.php" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.0.0 Safari/537.36"
192.168.0.102 - - [27/Feb/2023:17:04:59 +0000] "POST /wp-login.php HTTP/1.0" 200 2885 "https://local.com/wp-login.php" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.0.0 Safari/537.36"
These are default values, i made sure fail2ban is enabled and that i am not in the white list, but anyways i don't get banned while bruteforcing wp-admin