Hi guys,
Trying to remove the support for TLS 1.0 and 1.1 and enable only 1.2 and 1.3.
So far I did the following:
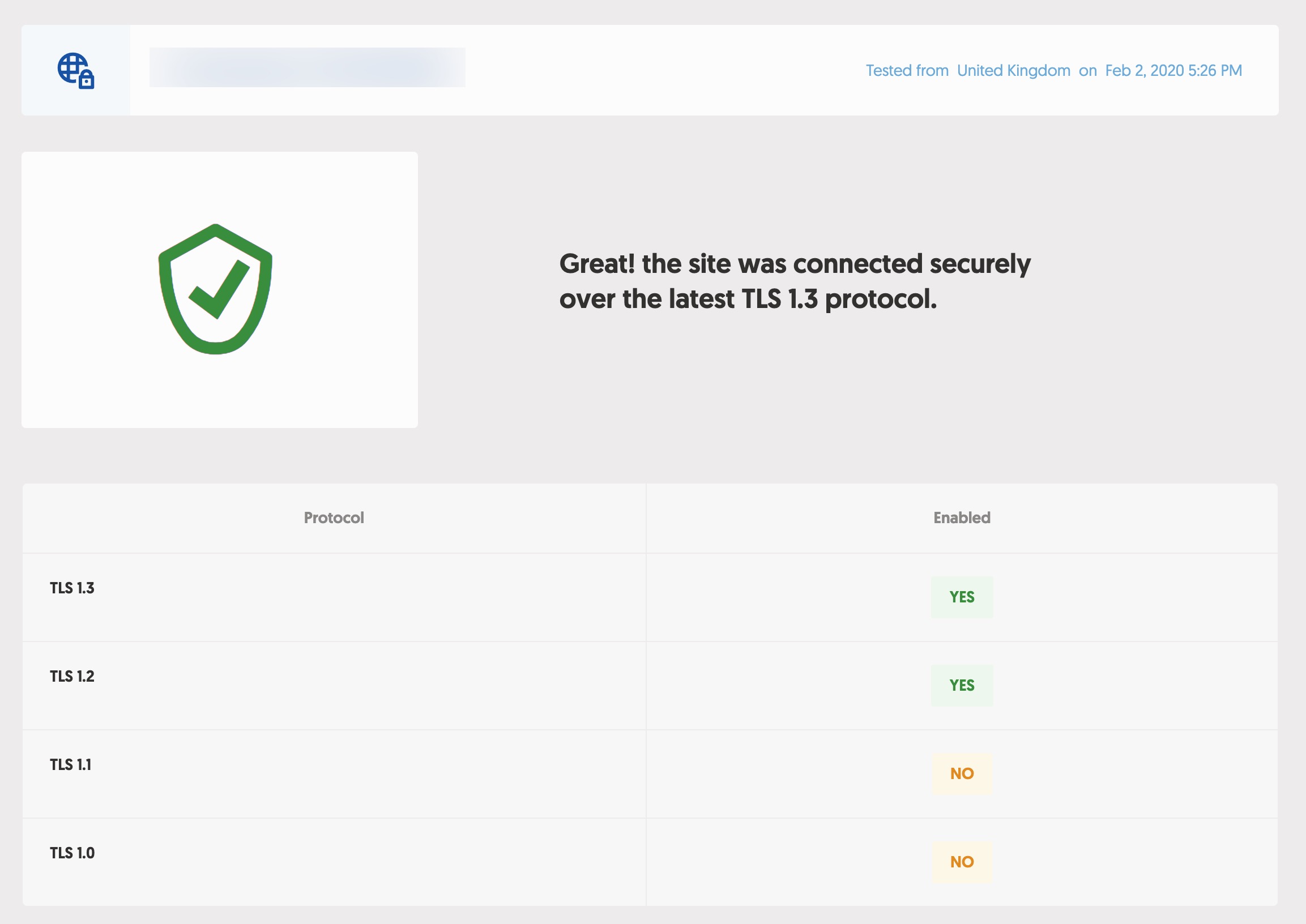
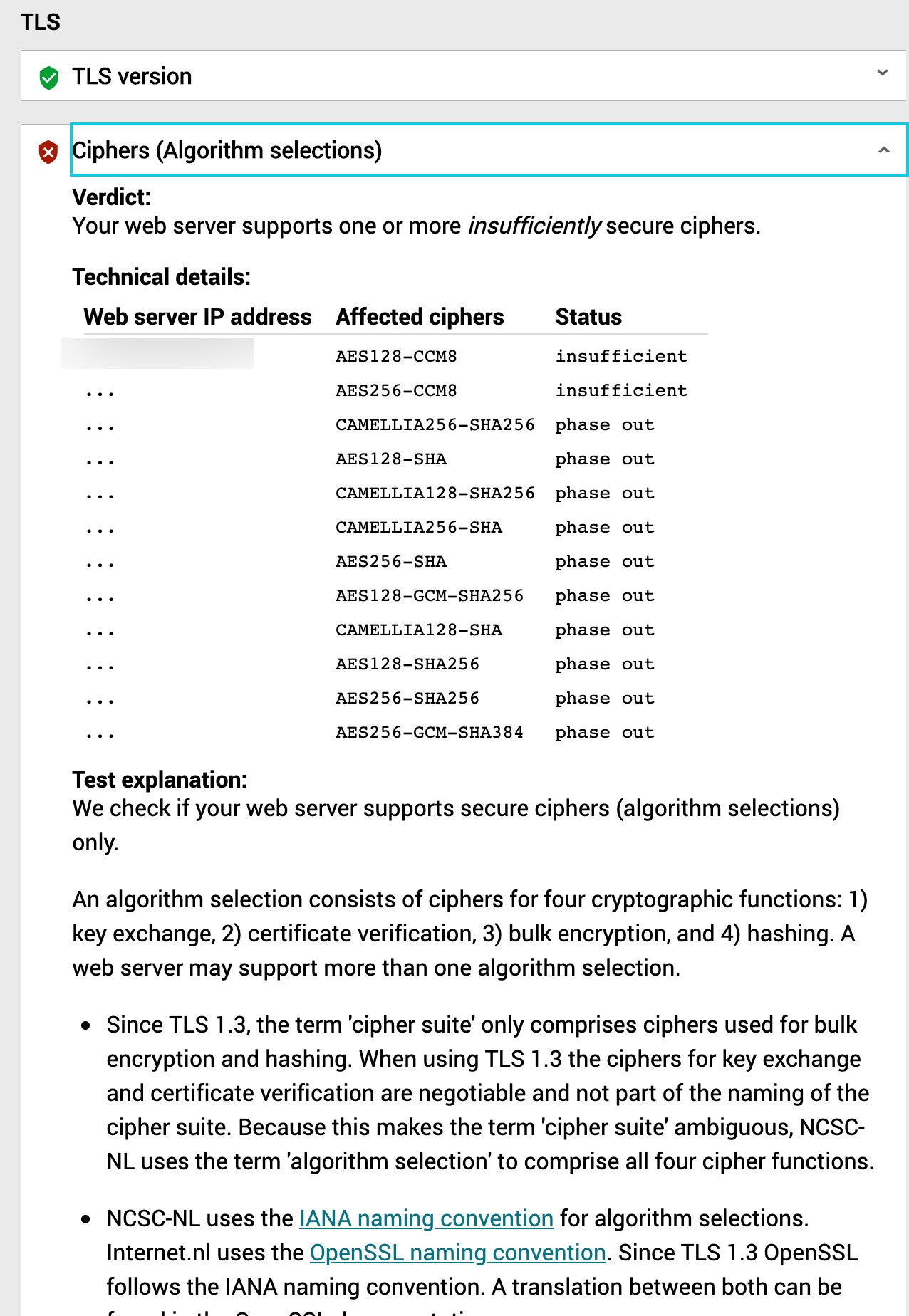
Checking on the domain level:
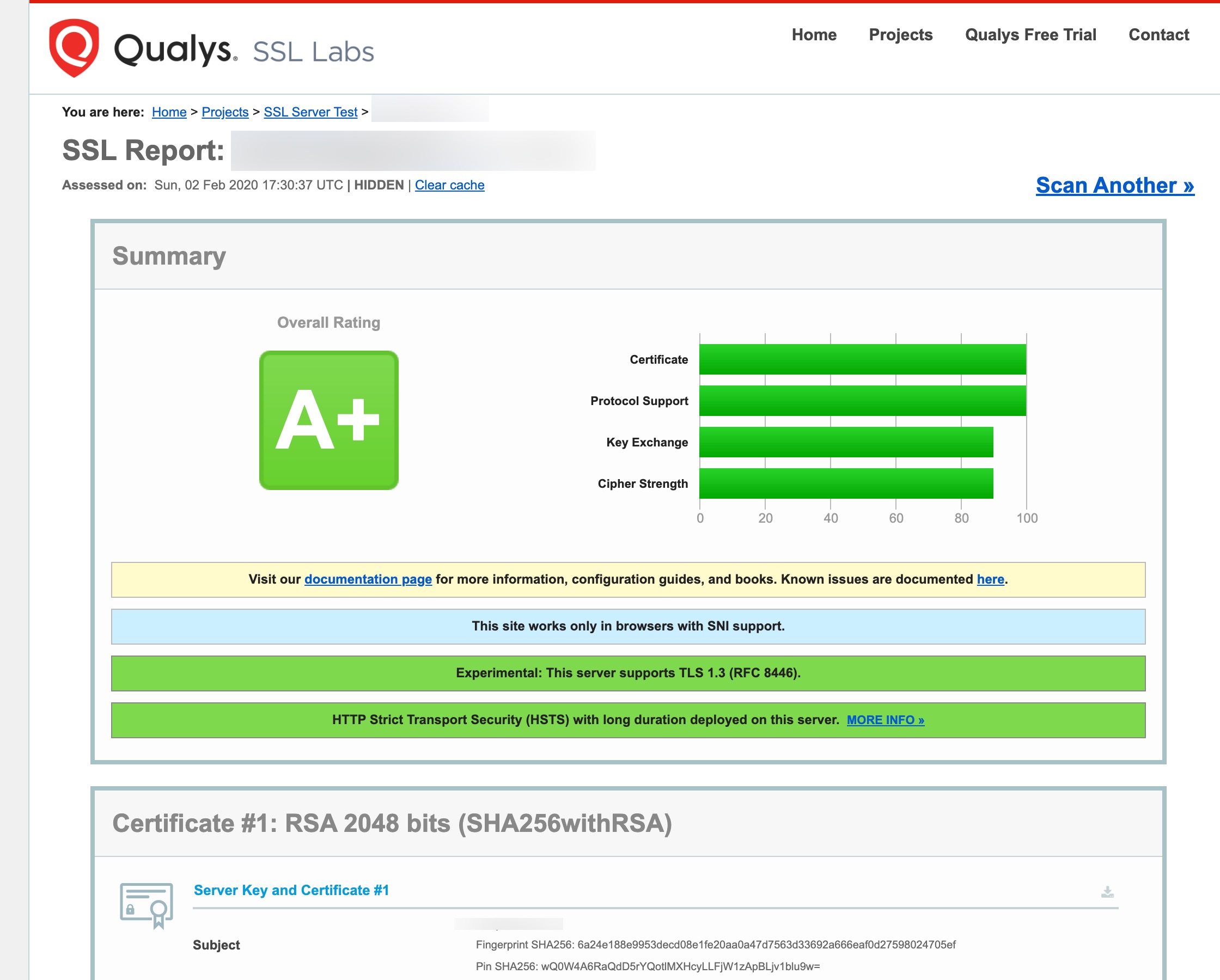
Server level seems fine:
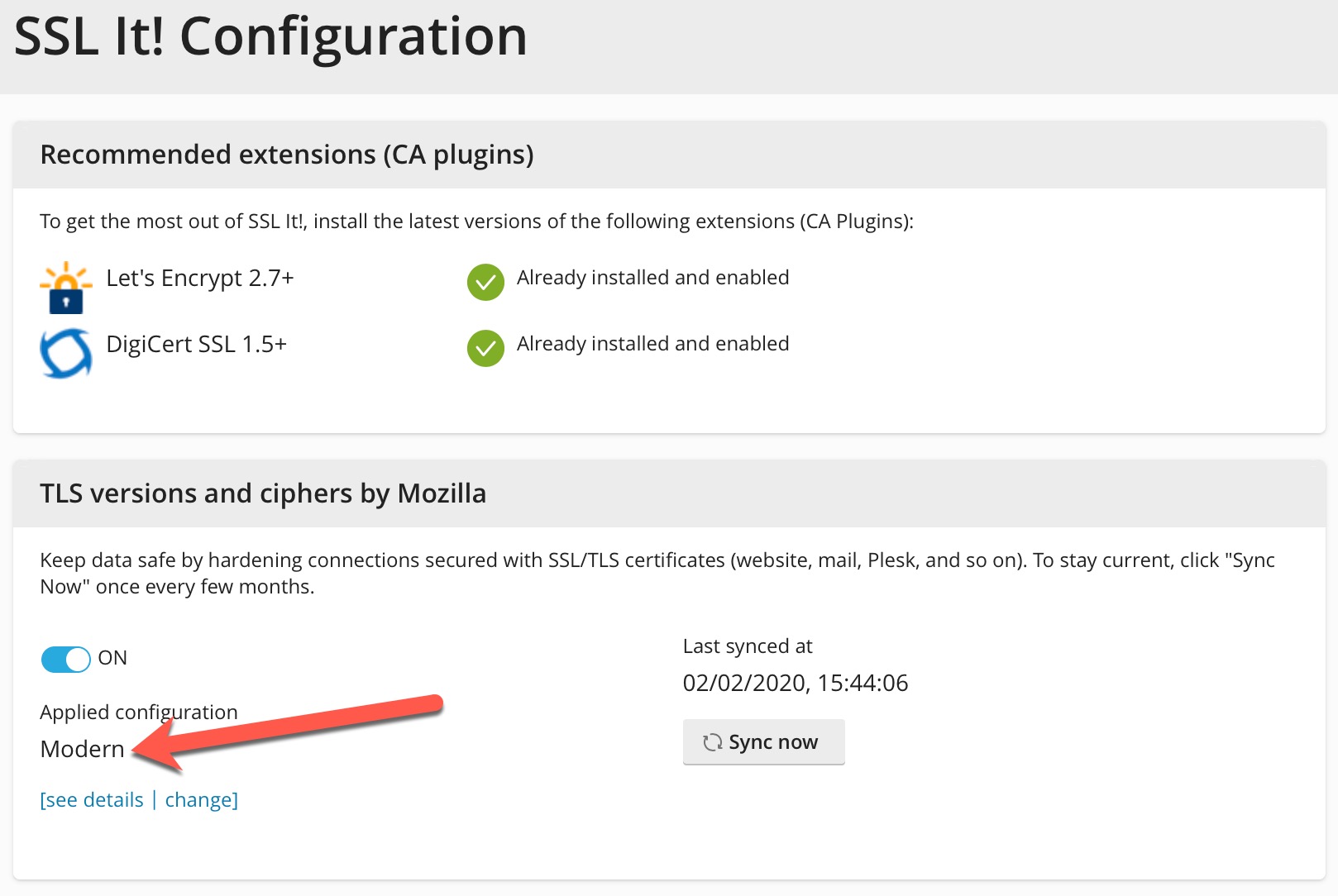
SSL It configuration is set on Modern:
What am I doing wrong?
Trying to remove the support for TLS 1.0 and 1.1 and enable only 1.2 and 1.3.
So far I did the following:
Code:
[root@ufo cache]# plesk bin server_pref -u -ssl-protocols 'TLSv1.2 TLSv1.3'
SUCCESS: Server preferences are successfully updated
[root@ufo cache]# /usr/local/psa/bin/server_pref -u -ssl-ciphers 'ECDHE-RSA-AES256-GCM-SHA512:DHE-RSA-AES256-GCM-SHA512:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384'
SUCCESS: Server preferences are successfully updated
[root@ufo cache]# service httpd restart
Redirecting to /bin/systemctl restart httpd.service
[root@ufo cache]# service nginx restart
Restarting nginx (via systemctl): [ OK ]Checking on the domain level:
Code:
[root@ufo cache]# nmap --script ssl-enum-ciphers -p 443 www.domain.com | grep -E "TLSv|SSLv"
| SSLv3: No supported ciphers found
| TLSv1.0:
| TLSv1.1:
| TLSv1.2:Server level seems fine:
Code:
[root@ufo cache]# /usr/local/psa/bin/server_pref -s | grep ssl-*
ssl-protocols: TLSv1.2 TLSv1.3
ssl-ciphers: ECDHE-RSA-AES256-GCM-SHA512:DHE-RSA-AES256-GCM-SHA512:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384
ssl-cipher-server-order: true
[root@ufo cache]#SSL It configuration is set on Modern:

What am I doing wrong?