Giorgos Kontopoulos
Basic Pleskian
I have installed the Lets encrypt extension and from the domain configuration (lets encrypt button) I have requested a certificate for that domain including protecting the www part of the website and when calling the https version of the website the certificate seems to work fine.
Its been advertised that ONYX now provides a easier setup of securing mail with SSL certificates
and sure enough in the MAIL SETTINGS of the same domain (smb/mail-settings/edit/id/2/domainId/2)
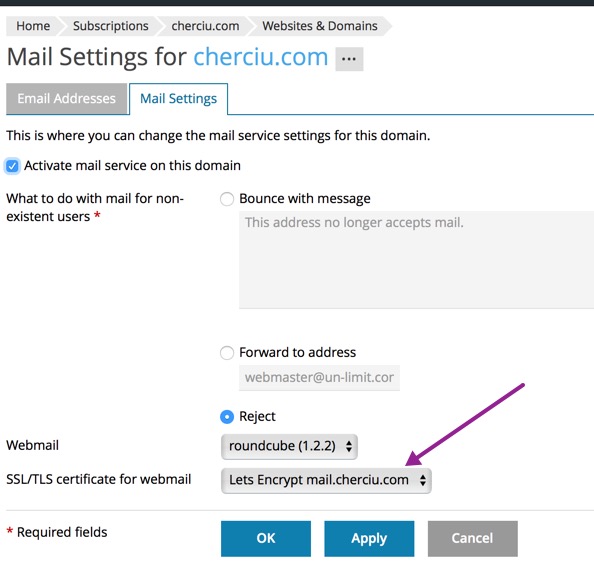
I see a select box "SSL/TLS certificate for webmail" and I chose the same certificate that was created for the domain.
NOTE:
- server1.domain2.tld is the hostname to the machine hosted at IP1
- MX record for domain.tld is mail.domain.tld with IP1 (same as the ip that plesk is running on)
Now trying to connect to email with Thunderbird
letting thunderbird autodetect everything comes up with unsecured connection to email and everything works using either of the following as the mail server hostnames
server1.domain2.tld
IP1
domain.tld
mail.domain.tld
and thunderbird finds pop3 at 110 port and smtp at 587 port
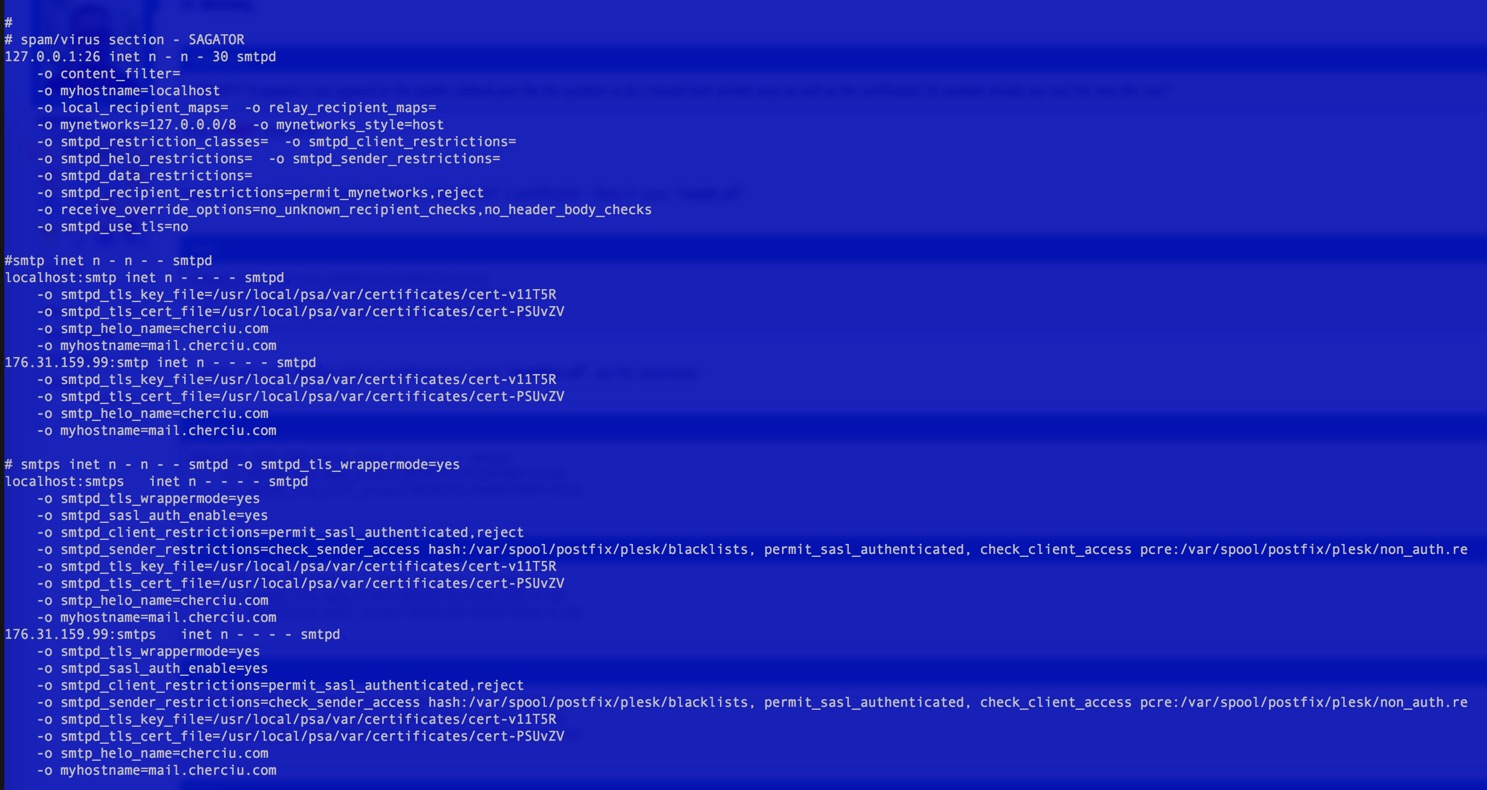
Now when I tell thunderbird to assume secure connection SSL/TLS the setup screen ALWAYS reports "Thunderbird failed to find the settings for your email account" for any hostname that I try
I tried all the 4 hostnames above
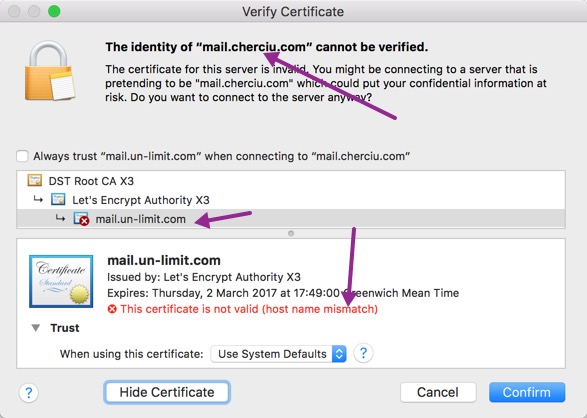
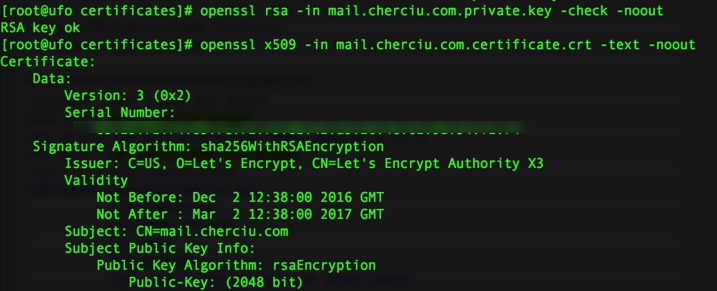
After that I created the subdomain in plesk mail.domain.tld and issued a certificate for it from Lets encrypt and tried to connect again with thunderbird but still getting failed message
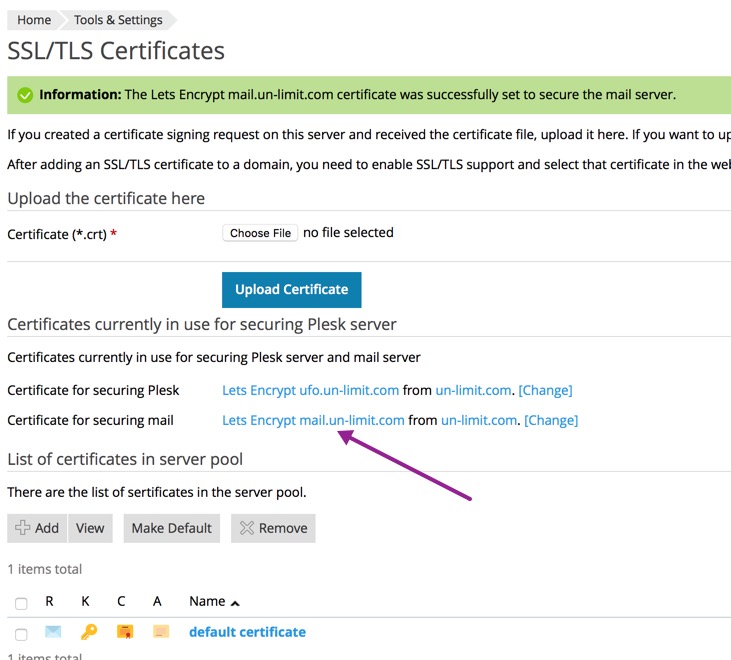
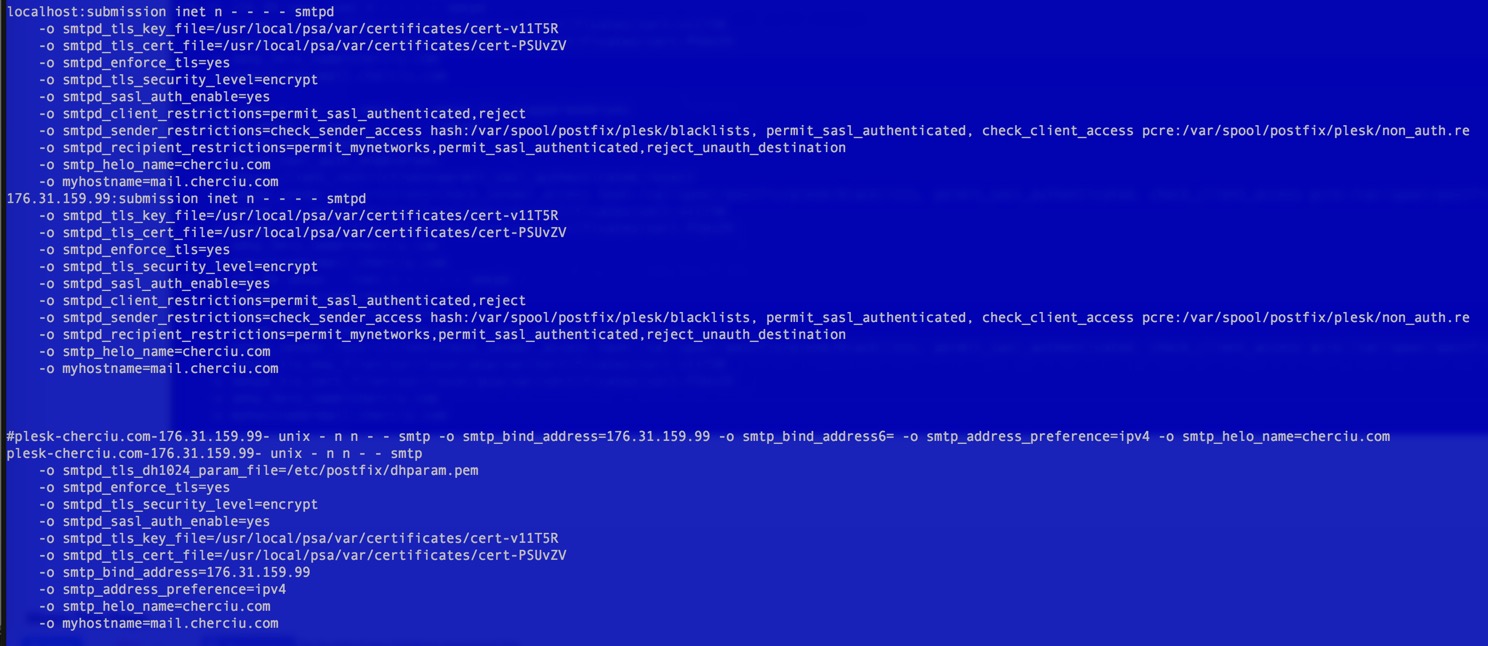
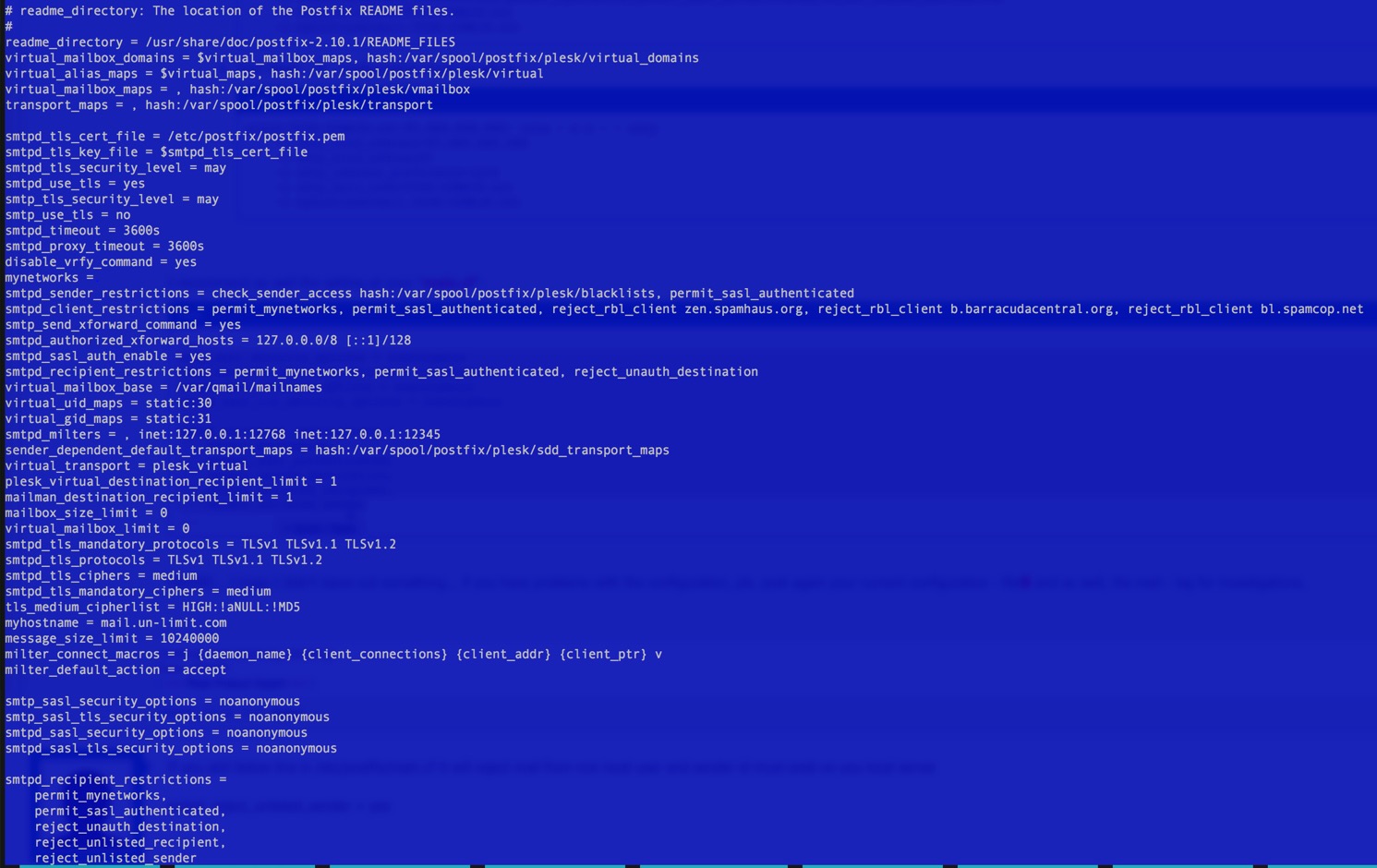
I have also gone to the SSL certificate settings and seen that one can set certificate for mail (admin/ssl-certificate/secure-mail-server) but which certificate should I choose there ?
mail.domain.tld
domain.tld
self signed certificate
I assume here I should choose a certificate for the server but choosing the self signed will ALWAYS give warning on all email clients since self signed has unrecognized certificate authority
How do I set this up ? do I need to setup this for email certificates to be working ?
What is the procedure of setting up SSL/TLS for mail in plesk ONYX ?
or is that a specific problem for lets encrypt certificates ?
Its been advertised that ONYX now provides a easier setup of securing mail with SSL certificates
and sure enough in the MAIL SETTINGS of the same domain (smb/mail-settings/edit/id/2/domainId/2)
I see a select box "SSL/TLS certificate for webmail" and I chose the same certificate that was created for the domain.
NOTE:
- server1.domain2.tld is the hostname to the machine hosted at IP1
- MX record for domain.tld is mail.domain.tld with IP1 (same as the ip that plesk is running on)
Now trying to connect to email with Thunderbird
letting thunderbird autodetect everything comes up with unsecured connection to email and everything works using either of the following as the mail server hostnames
server1.domain2.tld
IP1
domain.tld
mail.domain.tld
and thunderbird finds pop3 at 110 port and smtp at 587 port
Now when I tell thunderbird to assume secure connection SSL/TLS the setup screen ALWAYS reports "Thunderbird failed to find the settings for your email account" for any hostname that I try
I tried all the 4 hostnames above
After that I created the subdomain in plesk mail.domain.tld and issued a certificate for it from Lets encrypt and tried to connect again with thunderbird but still getting failed message
I have also gone to the SSL certificate settings and seen that one can set certificate for mail (admin/ssl-certificate/secure-mail-server) but which certificate should I choose there ?
mail.domain.tld
domain.tld
self signed certificate
I assume here I should choose a certificate for the server but choosing the self signed will ALWAYS give warning on all email clients since self signed has unrecognized certificate authority
How do I set this up ? do I need to setup this for email certificates to be working ?
What is the procedure of setting up SSL/TLS for mail in plesk ONYX ?
or is that a specific problem for lets encrypt certificates ?