After my server was restored, I added the following timeouts to /opt/psa/admin/conf/panel.ini
[ext-firewall]
confirmTimeout = 45
confirmTimeoutCli = 60
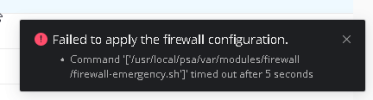
Alas, I still get the timeout error after 5s
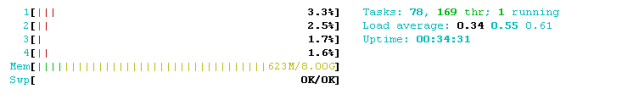
I did also check the processor load during run of the firewall script and I don't see any bottlenecks:
Here is the script which is prepared by the firewall extension, which also doesn't show any problems to me:
#!/bin/bash
#ATTENTION!
#
#DO NOT MODIFY THIS FILE BECAUSE IT WAS GENERATED AUTOMATICALLY,
#SO ALL YOUR CHANGES WILL BE LOST THE NEXT TIME THE FILE IS GENERATED.
set -e
([ -f /var/lock/subsys/ipchains ] && /etc/init.d/ipchains stop) >/dev/null 2>&1 || true
(rmmod ipchains) >/dev/null 2>&1 || true
apply_rule()
{
local iptables_bin="$1"
shift
local iptables_version
iptables_version="`"$iptables_bin" --version | awk '{print $2}' | awk -F. '{printf "%d%02d\n", $2, $3}'`"
# Use the native --wait option since v1.4.20
if [ "$iptables_version" -gt 420 ]; then
"$iptables_bin" -w "$@" 2>/dev/null
return $?
fi
# Emulate --wait for older versions
for i in `seq 10`; do
"$iptables_bin" "$@" 2>&1 | grep -q xtable || return 0
sleep 1
done
return 1
}
# Start of /usr/sbin/iptables setup
/usr/sbin/iptables-save -t filter | grep -- "-A INPUT" | grep -v "fail2ban-\|f2b-" | sed -e "s#^-A#apply_rule /usr/sbin/iptables -D#g" | while read -r cmd; do ${cmd} || true; done
apply_rule /usr/sbin/iptables -F FORWARD
apply_rule /usr/sbin/iptables -F OUTPUT
apply_rule /usr/sbin/iptables -Z FORWARD
apply_rule /usr/sbin/iptables -Z OUTPUT
apply_rule /usr/sbin/iptables -P INPUT DROP
apply_rule /usr/sbin/iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp ! --syn -m state --state NEW -j REJECT --reject-with tcp-reset
apply_rule /usr/sbin/iptables -A INPUT -m state --state INVALID -j DROP
apply_rule /usr/sbin/iptables -P OUTPUT DROP
apply_rule /usr/sbin/iptables -A OUTPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
apply_rule /usr/sbin/iptables -A OUTPUT -p tcp ! --syn -m state --state NEW -j REJECT --reject-with tcp-reset
apply_rule /usr/sbin/iptables -A OUTPUT -m state --state INVALID -j DROP
apply_rule /usr/sbin/iptables -P FORWARD DROP
apply_rule /usr/sbin/iptables -A FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPT
apply_rule /usr/sbin/iptables -A FORWARD -p tcp ! --syn -m state --state NEW -j REJECT --reject-with tcp-reset
apply_rule /usr/sbin/iptables -A FORWARD -m state --state INVALID -j DROP
apply_rule /usr/sbin/iptables -A INPUT -i lo -j ACCEPT
apply_rule /usr/sbin/iptables -A OUTPUT -o lo -j ACCEPT
apply_rule /usr/sbin/iptables -A FORWARD -i lo -o lo -j ACCEPT
apply_rule /usr/sbin/iptables -t mangle -F
apply_rule /usr/sbin/iptables -t mangle -Z
apply_rule /usr/sbin/iptables -t mangle -P PREROUTING ACCEPT
apply_rule /usr/sbin/iptables -t mangle -P OUTPUT ACCEPT
apply_rule /usr/sbin/iptables -t mangle -P INPUT ACCEPT
apply_rule /usr/sbin/iptables -t mangle -P FORWARD ACCEPT
apply_rule /usr/sbin/iptables -t mangle -P POSTROUTING ACCEPT
apply_rule /usr/sbin/iptables -t nat -F
apply_rule /usr/sbin/iptables -t nat -Z
apply_rule /usr/sbin/iptables -t nat -P PREROUTING ACCEPT
apply_rule /usr/sbin/iptables -t nat -P OUTPUT ACCEPT
apply_rule /usr/sbin/iptables -t nat -P POSTROUTING ACCEPT
# Start of /usr/sbin/ip6tables setup
/usr/sbin/ip6tables-save -t filter | grep -- "-A INPUT" | grep -v "fail2ban-\|f2b-" | sed -e "s#^-A#apply_rule /usr/sbin/ip6tables -D#g" | while read -r cmd; do ${cmd} || true; done
apply_rule /usr/sbin/ip6tables -F FORWARD
apply_rule /usr/sbin/ip6tables -F OUTPUT
apply_rule /usr/sbin/ip6tables -Z FORWARD
apply_rule /usr/sbin/ip6tables -Z OUTPUT
apply_rule /usr/sbin/ip6tables -P INPUT DROP
apply_rule /usr/sbin/ip6tables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp ! --syn -m state --state NEW -j REJECT --reject-with tcp-reset
apply_rule /usr/sbin/ip6tables -A INPUT -m state --state INVALID -j DROP
apply_rule /usr/sbin/ip6tables -P OUTPUT DROP
apply_rule /usr/sbin/ip6tables -A OUTPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
apply_rule /usr/sbin/ip6tables -A OUTPUT -p tcp ! --syn -m state --state NEW -j REJECT --reject-with tcp-reset
apply_rule /usr/sbin/ip6tables -A OUTPUT -m state --state INVALID -j DROP
apply_rule /usr/sbin/ip6tables -P FORWARD DROP
apply_rule /usr/sbin/ip6tables -A FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPT
apply_rule /usr/sbin/ip6tables -A FORWARD -p tcp ! --syn -m state --state NEW -j REJECT --reject-with tcp-reset
apply_rule /usr/sbin/ip6tables -A FORWARD -m state --state INVALID -j DROP
apply_rule /usr/sbin/ip6tables -A INPUT -i lo -j ACCEPT
apply_rule /usr/sbin/ip6tables -A OUTPUT -o lo -j ACCEPT
apply_rule /usr/sbin/ip6tables -A FORWARD -i lo -o lo -j ACCEPT
apply_rule /usr/sbin/ip6tables -t mangle -F
apply_rule /usr/sbin/ip6tables -t mangle -Z
apply_rule /usr/sbin/ip6tables -t mangle -P PREROUTING ACCEPT
apply_rule /usr/sbin/ip6tables -t mangle -P OUTPUT ACCEPT
apply_rule /usr/sbin/ip6tables -t mangle -P INPUT ACCEPT
apply_rule /usr/sbin/ip6tables -t mangle -P FORWARD ACCEPT
apply_rule /usr/sbin/ip6tables -t mangle -P POSTROUTING ACCEPT
apply_rule /usr/sbin/ip6tables -t nat -F
apply_rule /usr/sbin/ip6tables -t nat -Z
apply_rule /usr/sbin/ip6tables -t nat -P PREROUTING ACCEPT
apply_rule /usr/sbin/ip6tables -t nat -P OUTPUT ACCEPT
apply_rule /usr/sbin/ip6tables -t nat -P POSTROUTING ACCEPT
# Start of /usr/sbin/iptables rules
apply_rule /usr/sbin/iptables -A INPUT -p udp --dport 68 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -s 165.22.211.113 -j DROP
apply_rule /usr/sbin/iptables -A INPUT -s 177.223.175.170 -j DROP
apply_rule /usr/sbin/iptables -A INPUT -s 185.180.143.8 -j DROP
apply_rule /usr/sbin/iptables -A INPUT -s 186.211.1.7 -j DROP
apply_rule /usr/sbin/iptables -A INPUT -s 194.61.24.0/24 -j DROP
apply_rule /usr/sbin/iptables -A INPUT -s 212.70.149.0/24 -j DROP
apply_rule /usr/sbin/iptables -A INPUT -s 45.134.144.119 -j DROP
apply_rule /usr/sbin/iptables -A INPUT -s 46.148.40.0/24 -j DROP
apply_rule /usr/sbin/iptables -A INPUT -s 5.34.205.0/24 -j DROP
apply_rule /usr/sbin/iptables -A INPUT -s 5.34.207.0/24 -j DROP
apply_rule /usr/sbin/iptables -A INPUT -s 94.232.47.0/24 -j DROP
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 8443 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 8880 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 80 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 443 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 21 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 22 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 25 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 465 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 110 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 995 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 143 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 993 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 106 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 3306 -j DROP
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 5432 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p udp --dport 137 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p udp --dport 138 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 139 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 445 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p udp --dport 53 -j DROP
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 53 -j DROP
apply_rule /usr/sbin/iptables -A INPUT -p icmp --icmp-type 8/0 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -j ACCEPT
apply_rule /usr/sbin/iptables -A OUTPUT -j ACCEPT
apply_rule /usr/sbin/iptables -A FORWARD -j DROP
# End of /usr/sbin/iptables rules
# Start of /usr/sbin/ip6tables rules
apply_rule /usr/sbin/ip6tables -A INPUT -p udp --dport 546 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 8443 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 8880 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 80 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 443 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 21 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 22 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 25 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 465 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 110 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 995 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 143 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 993 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 106 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 3306 -j DROP
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 5432 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p udp --dport 137 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p udp --dport 138 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 139 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 445 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p udp --dport 53 -j DROP
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 53 -j DROP
apply_rule /usr/sbin/ip6tables -A INPUT -j ACCEPT
apply_rule /usr/sbin/ip6tables -A OUTPUT -j ACCEPT
apply_rule /usr/sbin/ip6tables -A FORWARD -j DROP
# End of /usr/sbin/ip6tables rules
#
# End of script
#


