Phantasia
Basic Pleskian
- Server operating system version
- Ubuntu 22.04.5 LTS
- Plesk version and microupdate number
- Plesk Obsidian v18.0.70_build1800250617.10 os_Ubuntu 22.04
Hello everyone,
I’m running Plesk Obsidian 18.0.70 on Ubuntu 22.04 and have recently started using Docker (e.g. to host Open WebUI).
Since then, I’ve noticed that a DROP rule against 172.17.0.2 (the Docker bridge IP) keeps getting automatically reinserted into the iptables INPUT chain – likely every 60 seconds or so:
This completely blocks external access to the container, even though it is behind a reverse proxy and should be reachable via HTTPS.
After some investigation, I traced the rule back to this script:
As a temporary workaround, I’ve created a cronjob that deletes the rule every minute – but the real issue persists in the background.
Important notes:
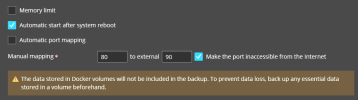
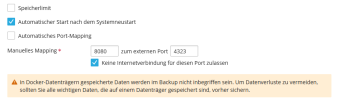
- I’ve created allow-rules for 172.17.0.2 via the Plesk Firewall GUI several times. They seem to have no effect.
- I’m on Docker 28.2.2, build e6534b4, so I’m well beyond the version where the known issue was supposedly fixed (see: this thread).
So my questions:
Any help or insight would be greatly appreciated!
I’m running Plesk Obsidian 18.0.70 on Ubuntu 22.04 and have recently started using Docker (e.g. to host Open WebUI).
Since then, I’ve noticed that a DROP rule against 172.17.0.2 (the Docker bridge IP) keeps getting automatically reinserted into the iptables INPUT chain – likely every 60 seconds or so:
Code:
DROP all -- 172.17.0.2 0.0.0.0/0This completely blocks external access to the container, even though it is behind a reverse proxy and should be reachable via HTTPS.
After some investigation, I traced the rule back to this script:
Code:
/opt/psa/var/modules/firewall/firewall-active.shAs a temporary workaround, I’ve created a cronjob that deletes the rule every minute – but the real issue persists in the background.
Important notes:
- I’ve created allow-rules for 172.17.0.2 via the Plesk Firewall GUI several times. They seem to have no effect.
- I’m on Docker 28.2.2, build e6534b4, so I’m well beyond the version where the known issue was supposedly fixed (see: this thread).
So my questions:
- Was the Docker fix in 28.0.1 only temporary or incomplete?
- Or is this an issue with Plesk Firewall rewriting rules incorrectly?
- Is there a proper (update-safe) way to allow internal Docker traffic via 172.17.x.x?
Any help or insight would be greatly appreciated!