- Server operating system version
- Debian 9.13
- Plesk version and microupdate number
- Version 18.0.44 Update #3
I don't know why, but lately I've been having the problem that suddenly, without any changes or really noticeable events in the logs, PHP just crashes and then only the following error is displayed in the access log:
Of course, every web request then receives a 502 error.
As soon as I restart MariaDB it works again.
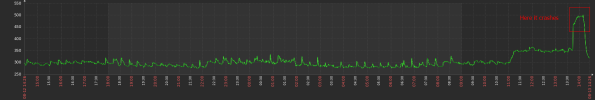
In my Zabbix monitoring environment I saw the following:
These are the processes:
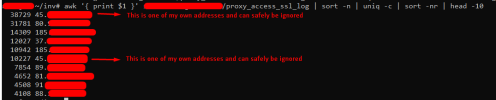
Otherwise nothing is unusual, does anyone have any idea which logs I can look at or what could be causing this error?
I set the setting "max_children" to 250, which should be fine for a 12 core and 32GB RAM.
25130#0: *26793910 connect() to unix:/var/www/vhosts/system/xxx.xxx.xxx/php-fpm.sock failed (11: Resource temporarily unavailable) while connecting to upstream |
Of course, every web request then receives a 502 error.
As soon as I restart MariaDB it works again.
In my Zabbix monitoring environment I saw the following:
These are the processes:

Otherwise nothing is unusual, does anyone have any idea which logs I can look at or what could be causing this error?
I set the setting "max_children" to 250, which should be fine for a 12 core and 32GB RAM.