- Server operating system version
- Ubuntu 22.04.3 on strato vServer
- Plesk version and microupdate number
- Plesk Obsidian Web Admin Edition Version 18.0.54 Update #4
I still have problems with the new plesk firewall.
After I set the timeouts in panel.ini to 120s I was able to activate the firewall and iptables -L did show all the rules.
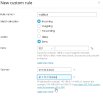
Then I tried to block two IP ranges by adding a block-all rule to deny all incoming ports for 218.92.0.0/24 and 61.177.172.0/24.
With the old firewall, it was very easy to do this.
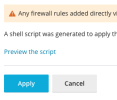
When I tried to activate my new rule, the firewall came back with the following error:
Failed to apply the firewall configuration.
The new firewall is much worse than the old one.
It is slower, the rule management is worse, and it does not work as properly as before.
After I set the timeouts in panel.ini to 120s I was able to activate the firewall and iptables -L did show all the rules.
Then I tried to block two IP ranges by adding a block-all rule to deny all incoming ports for 218.92.0.0/24 and 61.177.172.0/24.
With the old firewall, it was very easy to do this.
When I tried to activate my new rule, the firewall came back with the following error:
Failed to apply the firewall configuration.
- I did not receive connectivity confirmation after applying new firewall configuration, then same happened after I reverted to previous configuration. This means that both new and previous configurations were bad. Emergency rollback to configuration without rules was performed. Firewall is now disabled. Fix your rules and try again.
The new firewall is much worse than the old one.
It is slower, the rule management is worse, and it does not work as properly as before.