rubine2323
New Pleskian
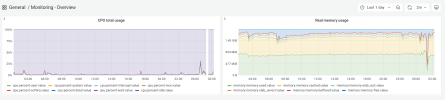
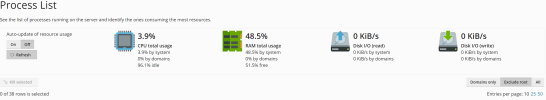
I ve the same issue like some people that plesk is crashing every now and then. The logs only show that:
The log suggests a few possible solutions to resolve the SELinux denial:
Any support knows if thats the cause of the random crashes?
I entered this issue in chatgpt because ive no clue how to fix it and chatgpt recommends me that:Jul 4 13:10:53 tender-borg setroubleshoot[196481]: SELinux is preventing /usr/sbin/sshd from open access on the file /etc/psa/.psa.shadow. For complete SELinux messages run: sealert -l 1d33a143-c6d1-41df-a8e7-075258f5f2ab
Jul 4 13:10:53 tender-borg setroubleshoot[196481]: SELinux is preventing /usr/sbin/sshd from open access on the file /etc/psa/.psa.shadow.
***** Plugin restorecon (99.5 confidence) suggests ************************
If you want to fix the label.
/etc/psa/.psa.shadow default label should be etc_t.
Then you can run restorecon. The access attempt may have been stopped due to insufficient permissions to access a parent directory, in which case try to change the following command accordingly.
Do
# /sbin/restorecon -v /etc/psa/.psa.shadow
***** Plugin catchall (1.49 confidence) suggests **************************
If you believe that sshd should be allowed open access on the .psa.shadow file by default.
Then you should report this as a bug.
You can generate a local policy module to allow this access.
Do
allow this access for now by executing:
# ausearch -c 'sshd' --raw | audit2allow -M my-sshd
# semodule -X 300 -i my-sshd.pp
Jul 4 13:11:01 tender-borg systemd[1]: Started Session 722 of User psaadm.
Jul 4 13:11:01 tender-borg systemd[1]: session-722.scope: Deactivated successfully.
Jul 4 13:11:02 tender-borg systemd[1]: dbus-:[email protected]: Deactivated successfully.
Jul 4 13:11:03 tender-borg systemd[1]: setroubleshootd.service: Deactivated successfully.
Jul 4 13:12:18 tender-borg systemd[1]: Starting SETroubleshoot daemon for processing new SELinux denial logs...
Jul 4 13:12:18 tender-borg systemd[1]: Started SETroubleshoot daemon for processing new SELinux denial logs.
Jul 4 13:12:18 tender-borg setroubleshoot[196532]: failed to retrieve rpm info for path '/etc/psa/.psa.shadow':
Jul 4 13:12:18 tender-borg systemd[1]: Started dbus-:[email protected].
Jul 4 13:12:19 tender-borg setroubleshoot[196532]: SELinux is preventing /usr/sbin/sshd from open access on the file /etc/psa/.psa.shadow. For complete SELinux messages run: sealert -l 1d33a143-c6d1-41df-a8e7-075258f5f2ab
Jul 4 13:12:19 tender-borg setroubleshoot[196532]: SELinux is preventing /usr/sbin/sshd from open access on the file /etc/psa/.psa.shadow.
***** Plugin restorecon (99.5 confidence) suggests ************************
If you want to fix the label.
/etc/psa/.psa.shadow default label should be etc_t.
Then you can run restorecon. The access attempt may have been stopped due to insufficient permissions to access a parent directory, in which case try to change the following command accordingly.
Do
# /sbin/restorecon -v /etc/psa/.psa.shadow
***** Plugin catchall (1.49 confidence) suggests **************************
If you believe that sshd should be allowed open access on the .psa.shadow file by default.
Then you should report this as a bug.
You can generate a local policy module to allow this access.
Do
allow this access for now by executing:
# ausearch -c 'sshd' --raw | audit2allow -M my-sshd
# semodule -X 300 -i my-sshd.pp
Jul 4 13:12:19 tender-borg setroubleshoot[196532]: SELinux is preventing /usr/sbin/sshd from open access on the file /etc/psa/.psa.shadow. For complete SELinux messages run: sealert -l 1d33a143-c6d1-41df-a8e7-075258f5f2ab
Jul 4 13:12:19 tender-borg setroubleshoot[196532]: SELinux is preventing /usr/sbin/sshd from open access on the file /etc/psa/.psa.shadow.
***** Plugin restorecon (99.5 confidence) suggests ************************
If you want to fix the label.
/etc/psa/.psa.shadow default label should be etc_t.
Then you can run restorecon. The access attempt may have been stopped due to insufficient permissions to access a parent directory, in which case try to change the following command accordingly.
Do
# /sbin/restorecon -v /etc/psa/.psa.shadow
***** Plugin catchall (1.49 confidence) suggests **************************
If you believe that sshd should be allowed open access on the .psa.shadow file by default.
Then you should report this as a bug.
You can generate a local policy module to allow this access.
Do
allow this access for now by executing:
# ausearch -c 'sshd' --raw | audit2allow -M my-sshd
# semodule -X 300 -i my-sshd.pp
Jul 4 13:12:29 tender-borg systemd[1]: dbus-:[email protected]: Deactivated successfully.
Jul 4 13:12:29 tender-borg systemd[1]: setroubleshootd.service: Deactivated successfully.
Jul 4 13:12:57 tender-borg NetworkManager[736]: <info> [1688476377.6671] dhcp4 (eth0): state changed new lease, address=212.227.224.43
The log suggests a few possible solutions to resolve the SELinux denial:
- Fix the label of the /etc/psa/.psa.shadow file by running the restorecon command:
bashCopy code
/sbin/restorecon -v /etc/psa/.psa.shadow - If the previous step doesn't resolve the issue, you can generate a local policy module to allow the necessary access:
perlCopy code
ausearch -c 'sshd' --raw | audit2allow -M my-sshd
semodule -X 300 -i my-sshd.pp - If you believe that the sshd process should be allowed open access to the .psa.shadow file by default, you can report this as a bug.
Any support knows if thats the cause of the random crashes?