Hello all,
In order to test the SPF protection I tried to send a email from another server changing the from to my domain... hopping that the SPF will block it but no. the email passed validations.
The email is coming from otherdomain.com but is delivered in [email protected] form [email protected], this should trigger SPF fail, right?
why is SPF checking otherdomain.com SPF and not the domain from the "from" field?
otherdomain.com has no SPF record at all
mydomain.com has a valid SPF record
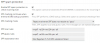
Email headers
Return-Path: <[email protected]>
Delivered-To: [email protected]
Received: from server7768.otherserver.com (otherdomain.com [213.229.106.xxx])
by LCSrv02.myserver.com (Postfix) with ESMTPS id A08C54361AE
for <[email protected]>; Mon, 10 Dec 2018 10:57:50 +0000 (GMT)
Authentication-Results: LCSrv02.myserver.com;
spf=pass (sender IP is 213.229.106.xxx) [email protected] smtp.helo=server7768.otherserver.com
Received-SPF: pass (LCSrv02.myserver.com: domain of otherdomain designates 213.229.106.xxx as permitted sender) client-ip=213.229.106.145; [email protected]; helo=server7768.otherserver.com;
Received: by server7768.otherserver.com (Postfix, from userid 10001)
id 5D2EA33B0794; Mon, 10 Dec 2018 10:57:50 +0000 (GMT)
To: [email protected]
Subject: SUBJECT FROM 3
X-PHP-Originating-Script: 10001:qwerty.php
to: [email protected] <[email protected]>
from: ruicadete@mydomain.com <ruicadete@mydomain.com>
Message-Id: ---
Date: Mon, 10 Dec 2018 10:57:50 +0000 (GMT)
In order to test the SPF protection I tried to send a email from another server changing the from to my domain... hopping that the SPF will block it but no. the email passed validations.
The email is coming from otherdomain.com but is delivered in [email protected] form [email protected], this should trigger SPF fail, right?
why is SPF checking otherdomain.com SPF and not the domain from the "from" field?
otherdomain.com has no SPF record at all
mydomain.com has a valid SPF record
Email headers
Return-Path: <[email protected]>
Delivered-To: [email protected]
Received: from server7768.otherserver.com (otherdomain.com [213.229.106.xxx])
by LCSrv02.myserver.com (Postfix) with ESMTPS id A08C54361AE
for <[email protected]>; Mon, 10 Dec 2018 10:57:50 +0000 (GMT)
Authentication-Results: LCSrv02.myserver.com;
spf=pass (sender IP is 213.229.106.xxx) [email protected] smtp.helo=server7768.otherserver.com
Received-SPF: pass (LCSrv02.myserver.com: domain of otherdomain designates 213.229.106.xxx as permitted sender) client-ip=213.229.106.145; [email protected]; helo=server7768.otherserver.com;
Received: by server7768.otherserver.com (Postfix, from userid 10001)
id 5D2EA33B0794; Mon, 10 Dec 2018 10:57:50 +0000 (GMT)
To: [email protected]
Subject: SUBJECT FROM 3
X-PHP-Originating-Script: 10001:qwerty.php
to: [email protected] <[email protected]>
from: ruicadete@mydomain.com <ruicadete@mydomain.com>
Message-Id: ---
Date: Mon, 10 Dec 2018 10:57:50 +0000 (GMT)


