Hi Guys,
Hope you could help shed some light.
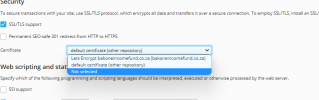
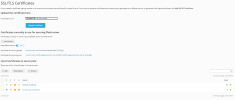
I'm running a Plesk CloudLinux server and I'm having trouble activating SSL's via the Lets Encrypt.
SSL IT! informs me the SSL has been installed correctly however upon reviewing the domain on the browser level it returns the following insecure errors:
NET::ERR_CERT_COMMON_NAME_INVALID
Hoping you can assist
Matthew J
Hope you could help shed some light.
I'm running a Plesk CloudLinux server and I'm having trouble activating SSL's via the Lets Encrypt.
SSL IT! informs me the SSL has been installed correctly however upon reviewing the domain on the browser level it returns the following insecure errors:
NET::ERR_CERT_COMMON_NAME_INVALID
Hoping you can assist
Matthew J