Hi again, thanks for the rapid answer.
There are two cases:
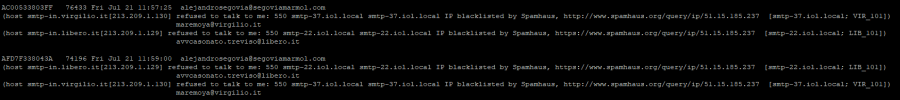
First case: E-mail is sended but after a second I receive a MAIL DELIVERY SYSTEM ERROR mail telling me that the mail was not delivered caused by the Spamhaus blacklist. The log of one e-mail rejected sent by Spamhaus:
Jul 22 22:08:32 amberserver postfix/smtpd[3199703]: connect from localhost.localdomain[::1]
Jul 22 22:08:32 amberserver postfix/smtpd[3199703]: TLS SNI localhost from localhost.localdomain[::1] not matched, using default chain
Jul 22 22:08:32 amberserver postfix/smtpd[3199703]: BCE2F33800A8: client=localhost.localdomain[::1], sasl_method=PLAIN, sasl_username=
[email protected]
Jul 22 22:08:32 amberserver psa-pc-remote[2154794]: BCE2F33800A8: from=<
[email protected]> to=<
[email protected]>
Jul 22 22:08:32 amberserver postfix/cleanup[3203148]: BCE2F33800A8: message-id=<
[email protected]>
Jul 22 22:08:32 amberserver psa-pc-remote[2154794]: BCE2F33800A8: py-limit-out: stderr: INFO:__main__:Setting 'X-PPP-Vhost' header to 'delope.es'
Jul 22 22:08:32 amberserver psa-pc-remote[2154794]: BCE2F33800A8: py-limit-out: stderr: PASS
Jul 22 22:08:33 amberserver psa-pc-remote[2154794]: BCE2F33800A8: spf: stderr: PASS
Jul 22 22:08:33 amberserver psa-pc-remote[2154794]: BCE2F33800A8: check-quota: stderr: SKIP
Jul 22 22:08:33 amberserver psa-pc-remote[2154794]: BCE2F33800A8: dk_sign: stderr: PASS
Jul 22 22:08:33 amberserver postfix/qmgr[2106400]: BCE2F33800A8: from=<
[email protected]>, size=1096, nrcpt=1 (queue active)
Jul 22 22:08:33 amberserver postfix/smtpd[3199703]: disconnect from localhost.localdomain[::1] ehlo=1 auth=1 mail=1 rcpt=1 data=1 quit=1 commands=6
Jul 22 22:08:33 amberserver dovecot: imap-login: Login: user=<
[email protected]>, method=PLAIN, rip=::1, lip=::1, mpid=3203632, TLS, session=<9pMd8hgBNtkAAAAAAAAAAAAAAAAAAAAB>
Jul 22 22:08:33 amberserver dovecot: service=imap, user=
[email protected], ip=[::1]. Disconnected: Logged out rcvd=977, sent=749
Jul 22 22:08:33 amberserver postfix/smtpd[3203365]: connect from localhost.localdomain[127.0.0.1]
Jul 22 22:08:33 amberserver postfix/smtpd[3203365]: 4C2B133800AB: client=localhost.localdomain[127.0.0.1], orig_queue_id=BCE2F33800A8, orig_client=localhost.localdomain[::1]
Jul 22 22:08:33 amberserver psa-pc-remote[2154794]: 4C2B133800AB: from=<
[email protected]> to=<
[email protected]>
Jul 22 22:08:33 amberserver postfix/cleanup[3203148]: 4C2B133800AB: message-id=<
[email protected]>
Jul 22 22:08:33 amberserver psa-pc-remote[2154794]: 4C2B133800AB: py-limit-out: stderr: INFO:__main__:No SMTP AUTH and not running in sendmail context (incoming or unrestricted outgoing mail). SKIP message.
Jul 22 22:08:33 amberserver psa-pc-remote[2154794]: 4C2B133800AB: py-limit-out: stderr: SKIP
Jul 22 22:08:33 amberserver psa-pc-remote[2154794]: 4C2B133800AB: spf: stderr: PASS
Jul 22 22:08:33 amberserver psa-pc-remote[2154794]: 4C2B133800AB: check-quota: stderr: SKIP
Jul 22 22:08:33 amberserver psa-pc-remote[2154794]: 4C2B133800AB: dk_sign: stderr: PASS
Jul 22 22:08:33 amberserver postfix/qmgr[2106400]: 4C2B133800AB: from=<
[email protected]>, size=2634, nrcpt=1 (queue active)
Jul 22 22:08:33 amberserver postfix/smtpd[3203365]: disconnect from localhost.localdomain[127.0.0.1] ehlo=1 xforward=1 mail=1 rcpt=1 data=1 quit=1 commands=6
Jul 22 22:08:33 amberserver amavis[2935938]: (2935938-17) Passed CLEAN {RelayedInbound}, [::1]:42710 <
[email protected]> -> <
[email protected]>, Queue-ID: BCE2F33800A8, Message-ID: <
[email protected]>, mail_id: aTJEqrD22qWV, Hits: -1.108, size: 1745, queued_as: 4C2B133800AB, 387 ms
Jul 22 22:08:33 amberserver postfix/smtp[3203158]: BCE2F33800A8: to=<
[email protected]>, relay=127.0.0.1[127.0.0.1]:10024, delay=0.73, delays=0.33/0/0/0.39, dsn=2.0.0, status=sent (250 2.0.0 from MTA(smtp:[127.0.0.1]:10025): 250 2.0.0 Ok: queued as 4C2B133800AB)
Jul 22 22:08:33 amberserver postfix/qmgr[2106400]: BCE2F33800A8: removed
Jul 22 22:08:33 amberserver dovecot: imap-login: Login: user=<
[email protected]>, method=PLAIN, rip=::1, lip=::1, mpid=3203643, TLS, session=<GLIo8hgBQtkAAAAAAAAAAAAAAAAAAAAB>
Jul 22 22:08:33 amberserver dovecot: service=imap, user=
[email protected], ip=[::1]. Disconnected: Logged out rcvd=74, sent=2158
Jul 22 22:08:34 amberserver postfix/smtpd[3196269]: lost connection after AUTH from unknown[46.148.40.199]
Jul 22 22:08:34 amberserver postfix/smtpd[3196269]: disconnect from unknown[46.148.40.199] ehlo=1 auth=0/1 rset=1 commands=2/3
Jul 22 22:08:34 amberserver dovecot: imap-login: Login: user=<
[email protected]>, method=PLAIN, rip=::1, lip=::1, mpid=3203645, TLS, session=<dV4t8hgBRNkAAAAAAAAAAAAAAAAAAAAB>
Jul 22 22:08:34 amberserver dovecot: service=imap, user=
[email protected], ip=[::1]. Disconnected: Logged out rcvd=502, sent=35019
Jul 22 22:08:34 amberserver postfix/smtp[3203169]: 4C2B133800AB: to=<
[email protected]>, relay=hotmail-com.olc.protection.outlook.com[104.47.56.161]:25, delay=1.4, delays=0.17/0/1.1/0.15, dsn=5.7.1, status=bounced (host hotmail-com.olc.protection.outlook.com[104.47.56.161] said: 550 5.7.1 Service unavailable, Client host [51.15.185.237] blocked using Spamhaus. To request removal from this list see
https://www.spamhaus.org/query/ip/51.15.185.237 (AS3130). [CO1NAM11FT023.eop-nam11.prod.protection.outlook.com 2023-07-22T20:08:34.625Z 08DB8AD501D09E7F] (in reply to MAIL FROM command))
Jul 22 22:08:34 amberserver postfix/smtp[3203169]: 4C2B133800AB: lost connection with hotmail-com.olc.protection.outlook.com[104.47.56.161] while sending RCPT TO
Jul 22 22:08:34 amberserver postfix/cleanup[3203148]: B4CFA33800AE: message-id=<
[email protected]>
Jul 22 22:08:34 amberserver postfix/bounce[3203170]: 4C2B133800AB: sender non-delivery notification: B4CFA33800AE
Jul 22 22:08:34 amberserver postfix/qmgr[2106400]: B4CFA33800AE: from=<>, size=5319, nrcpt=1 (queue active)
Jul 22 22:08:34 amberserver postfix/qmgr[2106400]: 4C2B133800AB: removed
Jul 22 22:08:34 amberserver postfix-local[3203647]: B4CFA33800AE: from=<MAILER-DAEMON>, to=<
[email protected]>, dirname=/var/qmail/mailnames
Jul 22 22:08:34 amberserver dk_check[3203649]: B4CFA33800AE: DKIM Feed: No signature
Jul 22 22:08:34 amberserver postfix-local[3203647]: B4CFA33800AE: dk_check: stderr: PASS
Jul 22 22:08:34 amberserver dmarc[3203650]: B4CFA33800AE: SPF record was not found in Authentication-Results
Jul 22 22:08:34 amberserver postfix-local[3203647]: B4CFA33800AE: dmarc: stderr: PASS
Jul 22 22:08:34 amberserver dovecot: service=lda, user=
[email protected], ip=[]. Warning: Failed to parse return-path header
Jul 22 22:08:34 amberserver dovecot: service=lda, user=
[email protected], ip=[]. sieve: msgid=<
[email protected]>: stored mail into mailbox 'INBOX'
Jul 22 22:08:34 amberserver postfix/pipe[3203171]: B4CFA33800AE: to=<
[email protected]>, relay=plesk_virtual, delay=0.15, delays=0.01/0/0/0.13, dsn=2.0.0, status=sent (delivered via plesk_virtual service)
Jul 22 22:08:34 amberserver postfix/qmgr[2106400]: B4CFA33800AE: removed
Jul 22 22:08:35 amberserver dovecot: imap-login: Login: user=<
[email protected]>, method=PLAIN, rip=::1, lip=::1, mpid=3203657, TLS, session=<DoU88hgBqJkAAAAAAAAAAAAAAAAAAAAB>
Jul 22 22:08:35 amberserver dovecot: service=imap, user=
[email protected], ip=[::1]. Disconnected: Logged out rcvd=130, sent=2216
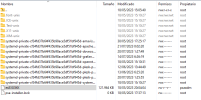
Second case: The e-mail is not sended and is in the mail pending queue. I attach a image when use the command "postqueue -p".
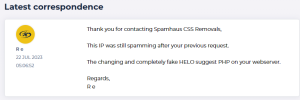
These examples are of normal e-mails sent through webmail. I do not identify in the logs any email sent with HELO value "outlook.com" as indicated in the screenshot of my previous Spamhaus post.
Thanks.