Dukemaster
Regular Pleskian
Hi at all,
by the great help of PLESK Support Articles in this community I successfully activated HSTS globally since half a year on Ubuntu 14 and 16 by 001_own_additional_ssl_hsts_.conf in etc/nginx/conf.d
All 8 domains on server get the result on SSLLABS.
Last week a made a test again and was surprised that HSTS is not working any longer (not with & without www.)
Can You please me finding out why and how to set up again.
I can only imagine why it isn't working:
My changes the last weeks.
Setting successfully OSCP stapling (but I'm relative sure that it worked after this).
Setting net/interface primary IPv4 from DHCP to static and installing two IPv4 for DNS setup
[Own DNS is working since yesterday. "THANKS A LOT @UFHH01 " ! ! !]
Removing IPv6 from webhosting settings of all domains and also in providers domain panel, but IPv6 is still on Plesk and server in background. I'm too afraid removing it totally from PLESK to loose everything (connection/access).
Running Plesk reconfigurator tutorial.
Created an x_y_z_mapping.txt (don't know the exactly name which was located in /<root>/root and deleted it afterwards again, sorry I don't know the tutorial and why. nor if the tutorial came from 1and1 or Plesk. but it had to do with IP related things. sorry to have only these less infos.
Setup is Ubuntu 16.04.2 with Apache and Nginx as Reverse Proxy.
nginx -t absolutely ok
Lots of greets
by the great help of PLESK Support Articles in this community I successfully activated HSTS globally since half a year on Ubuntu 14 and 16 by 001_own_additional_ssl_hsts_.conf in etc/nginx/conf.d
All 8 domains on server get the result on SSLLABS.
ssl_session_timeout 10m;
ssl_session_cache shared:SSL:50m;
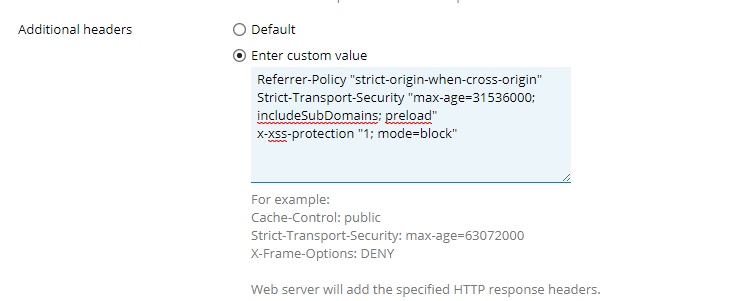
add_header X-Frame-Options SAMEORIGIN;
add_header X-XSS-Protection "1; mode=block";
add_header X-Content-Type-Options nosniff;
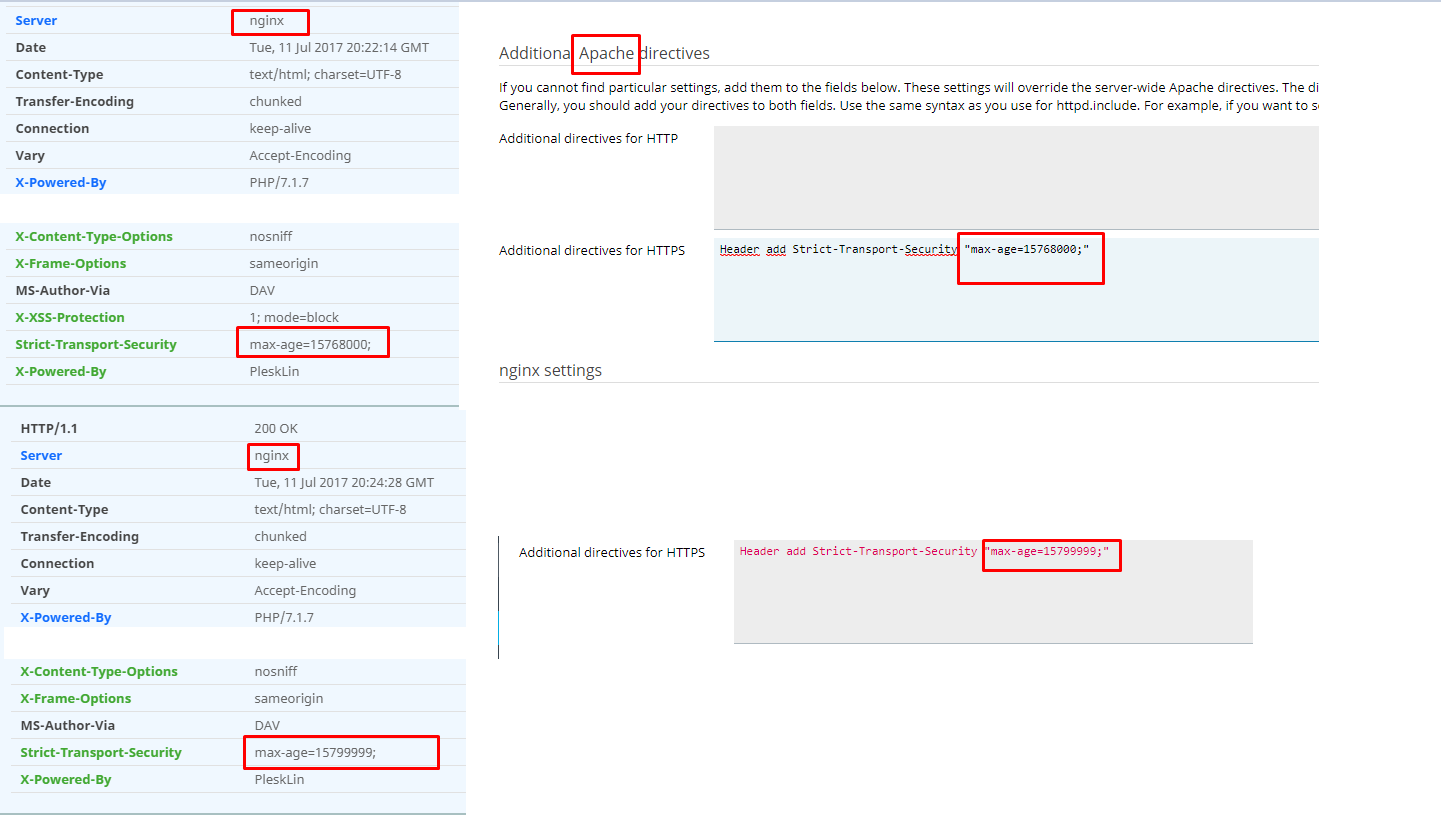
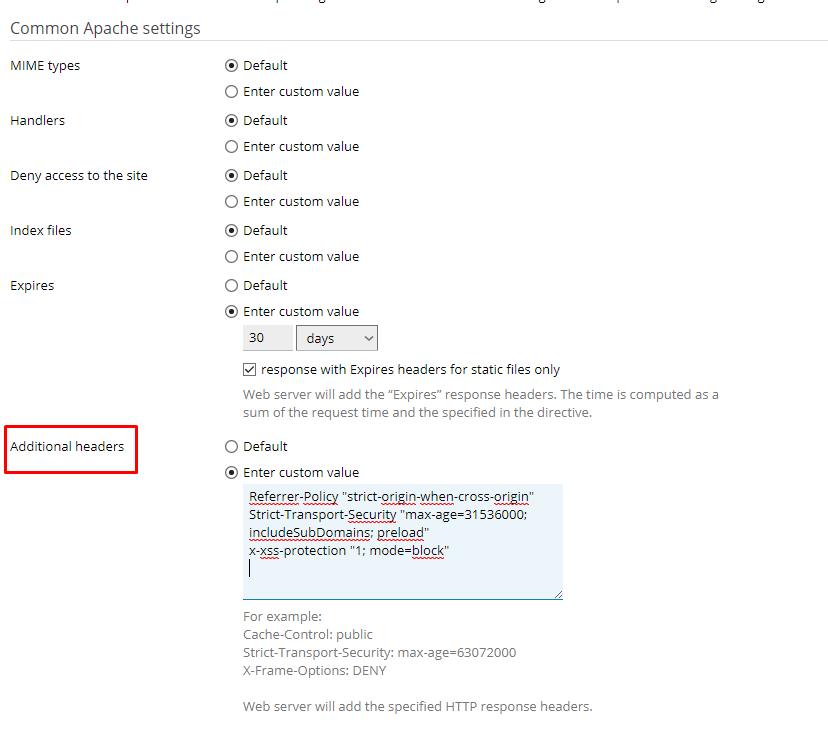
add_header Strict-Transport-Security 'max-age=15768000;includeSubDomains';
Last week a made a test again and was surprised that HSTS is not working any longer (not with & without www.)
Can You please me finding out why and how to set up again.
I can only imagine why it isn't working:
My changes the last weeks.
Setting successfully OSCP stapling (but I'm relative sure that it worked after this).
Setting net/interface primary IPv4 from DHCP to static and installing two IPv4 for DNS setup
[Own DNS is working since yesterday. "THANKS A LOT @UFHH01 " ! ! !]
Removing IPv6 from webhosting settings of all domains and also in providers domain panel, but IPv6 is still on Plesk and server in background. I'm too afraid removing it totally from PLESK to loose everything (connection/access).
Running Plesk reconfigurator tutorial.
Created an x_y_z_mapping.txt (don't know the exactly name which was located in /<root>/root and deleted it afterwards again, sorry I don't know the tutorial and why. nor if the tutorial came from 1and1 or Plesk. but it had to do with IP related things. sorry to have only these less infos.
Setup is Ubuntu 16.04.2 with Apache and Nginx as Reverse Proxy.
nginx -t absolutely ok
# curl -v ~ Super World | Start ~
* Rebuilt URL to: ~ Super World | Start ~
* Trying 217.160.92.49...
* Connected to domain.com (217.160.92.49) port 443 (#0)
* found 173 certificates in /etc/ssl/certs/ca-certificates.crt
* found 696 certificates in /etc/ssl/certs
* ALPN, offering http/1.1
* SSL connection using TLS1.2 / ECDHE_RSA_AES_128_GCM_SHA256
* server certificate verification OK
* server certificate status verification SKIPPED
* common name: domain.com (matched)
* server certificate expiration date OK
* server certificate activation date OK
* certificate public key: RSA
* certificate version: #3
* subject: CN=domain.com
* start date: Wed, 07 Jun 2017 00:19:00 GMT
* expire date: Tue, 05 Sep 2017 00:19:00 GMT
* issuer: C=US,O=Let's Encrypt,CN=Let's Encrypt Authority X3
* compression: NULL
* ALPN, server accepted to use http/1.1
> GET / HTTP/1.1
> Host: domain.com
> User-Agent: curl/7.47.0
> Accept: */*
>
< HTTP/1.1 301 Moved Permanently
< Server: nginx
< Date: Fri, 07 Jul 2017 12:13:20 GMT
< Content-Type: text/html
< Content-Length: 178
< Connection: keep-alive
< Location: ~ Super World | Start ~
< X-Powered-By: PleskLin
<
<html>
<head><title>301 Moved Permanently</title></head>
<body bgcolor="white">
<center><h1>301 Moved Permanently</h1></center>
<hr><center>nginx</center>
</body>
</html>
* Connection #0 to host domain.com left intact
Lots of greets
Last edited: