marvin
Basic Pleskian
- Server operating system version
- Centos 7
- Plesk version and microupdate number
- Plesk Obidian 18.0
I'm asking this question again in order to (hopefully) generate more discussion and hopefully resolve my issue.
Late May this year the LetsEncrypt Security certificate on my domain expired and auto-renewed. The resulting chain of events caused a lot of angst and service disruption that I won't go into here, but after reading posts on this forum, checking ports, looking at settings, changing passwords and much faffing about I've arrived at the situation where we have two email accounts with POP and SMTP service on Mac Mail and Thunderbird.
IMAP for webmail and phone service is another matter. We are unable to receive emails on our phones but we can send email.
Logging in to Roundcube webmail on Firefox produces the following error:
Chrome tells me:
Which would seem to point to a Security Certificate Issue (unless this is a generic error message?).
While Safari shows me a Plesk Web Server Default Page (it says in the address bar that this page is not secure).
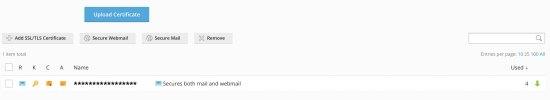
Keeping in mind that everything was working fine until the expiry of the LetsEncrypt certificate for MySite.co.nz -- and that since the auto-renew I've gone in again and renewed LetsEncrypt certificate manually (including certificates for Mail, Webmail and *Wildcard) -- can anybody shed any light on what''s gone amiss?
What is this ERR_CERT_COMMON_NAME_INVALID of which Plesk speaks?
Note: This only seems to affect ONE domain on my VPS. Other co-hosted domains are functioning normally.
Late May this year the LetsEncrypt Security certificate on my domain expired and auto-renewed. The resulting chain of events caused a lot of angst and service disruption that I won't go into here, but after reading posts on this forum, checking ports, looking at settings, changing passwords and much faffing about I've arrived at the situation where we have two email accounts with POP and SMTP service on Mac Mail and Thunderbird.
IMAP for webmail and phone service is another matter. We are unable to receive emails on our phones but we can send email.
Logging in to Roundcube webmail on Firefox produces the following error:
Did Not Connect: Potential Security Issue
Firefox detected a potential security threat and did not continue to webmail.mysite.co.nz because this website requires a secure connection.
What can you do about it?
webmail.mysite.co.nz has a security policy called HTTP Strict Transport Security (HSTS), which means that Firefox can only connect to it securely. You can’t add an exception to visit this site.
The issue is most likely with the website, and there is nothing you can do to resolve it. You can notify the website’s administrator about the problem.
Chrome tells me:
Attackers might be trying to steal your information from webmail.mysite.co.nz (for example, passwords, messages or credit cards). Learn more
Your connection is not private
NET::ERR_CERT_COMMON_NAME_INVALID
Which would seem to point to a Security Certificate Issue (unless this is a generic error message?).
While Safari shows me a Plesk Web Server Default Page (it says in the address bar that this page is not secure).
Keeping in mind that everything was working fine until the expiry of the LetsEncrypt certificate for MySite.co.nz -- and that since the auto-renew I've gone in again and renewed LetsEncrypt certificate manually (including certificates for Mail, Webmail and *Wildcard) -- can anybody shed any light on what''s gone amiss?
What is this ERR_CERT_COMMON_NAME_INVALID of which Plesk speaks?
Note: This only seems to affect ONE domain on my VPS. Other co-hosted domains are functioning normally.