Hello
Since last night we have display errors on all our Plesk 12.5 servers on the Let's Encrypt extension.
* Steps to reproduce:
1) Logon to Plesk
2) Pick a domain
3) Click on "Let's Encrypt"
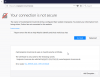
The page is then display as follows:
OS: CentOS 7.4.1708
Plesk version: 12.5.30 Update #74
Let's Encrypt version: 2.5.1 Release 344
We don't see this issue with our Plesk Onyx 17.5 servers.
Anybody else having the same issue?
Since last night we have display errors on all our Plesk 12.5 servers on the Let's Encrypt extension.
* Steps to reproduce:
1) Logon to Plesk
2) Pick a domain
3) Click on "Let's Encrypt"
The page is then display as follows:

OS: CentOS 7.4.1708
Plesk version: 12.5.30 Update #74
Let's Encrypt version: 2.5.1 Release 344
We don't see this issue with our Plesk Onyx 17.5 servers.
Anybody else having the same issue?