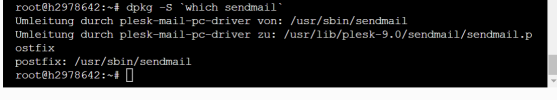
- Server operating system version
- ubuntu 20.04
- Plesk version and microupdate number
- Plesk Obsidian Web Admin Edition 18.0.58 Update Nr. 2
Hello guys,
I want the SMTP server to use the 587 port instead 25. So for security reason we want to use secure connection for outgoing emails.
I already read this topic, as well.
 talk.plesk.com
talk.plesk.com
On my main.cf file there is no such as configuration entry which is mentioned on post.
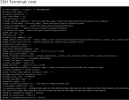
Is there any body who can help me ?
Best regards,
Thanks in advance!
Hasan
I want the SMTP server to use the 587 port instead 25. So for security reason we want to use secure connection for outgoing emails.
I already read this topic, as well.
Question - Change default SMTP Port in Plesk
Hi, I have noticed Plesk use default 25 port for sending mail. Unfortunately, my server provider blocks port 25 by default. When i asked them they says to use 465, 587, or 2525 instead of 25. How to change the default port?
 talk.plesk.com
talk.plesk.com
On my main.cf file there is no such as configuration entry which is mentioned on post.

Is there any body who can help me ?
Best regards,
Thanks in advance!
Hasan